Preventing SQL Injection (SQLi) in Symfony: Essential Tips for Web Security
SQL Injection (SQLi) for Symfony: Practical Tips with Code Examples
SQL Injection (SQLi) is a common attack in web applications that allows hackers to manipulate SQL queries, often gaining unauthorized access to sensitive information. For developers using Symfony, understanding how to prevent SQL Injection is critical for building secure applications. This guide will walk you through SQLi protection techniques specific to Symfony with code examples and tools.
What is SQL Injection (SQLi)?
SQL Injection happens when a user inputs SQL code into a form field, like a login or search bar, to manipulate the database. For instance, in an application where a username and password are directly included in a SQL query, an attacker could enter ' OR 1=1 -- to bypass login requirements and access restricted areas.
How SQL Injection Impacts Symfony Applications
Symfony applications often use Doctrine ORM or the Symfony Query Builder for database interactions. These tools offer built-in mechanisms to protect against SQLi, but improper coding practices can leave vulnerabilities.
SQLi Prevention Techniques for Symfony: Code Examples
Below are key steps to protect your Symfony application from SQL Injection, with code examples to illustrate best practices.
1. Use Prepared Statements with Doctrine ORM
Using prepared statements is the safest way to prevent SQL Injection because it separates SQL logic from data. Here’s how to use Doctrine’s createQueryBuilder with prepared statements:
In this example, setParameter escapes the $id variable, preventing any SQL commands from executing maliciously.
2. Use Symfony’s Input Validation
Validate all user inputs to ensure they meet the expected format, such as numeric-only IDs or specific string patterns. Symfony offers a robust validator component:
This code checks that $id is an integer before it’s used in a database query, reducing the risk of SQL Injection.
3. Escape Inputs Properly
Symfony’s Twig templating engine automatically escapes output by default, but it’s always best to check manually. For instance:
The |e filter escapes the output, preventing any malicious input from executing.
4. Limit Database Privileges
Ensure your database user has limited privileges, only enough to perform required tasks. For instance, avoid giving write access for read-only operations. By managing permissions effectively, even if an SQLi attack occurs, the potential damage is minimized.
Tools for Vulnerability Assessment
To ensure your application is secure from SQLi vulnerabilities, run regular vulnerability assessments. We offer free cybersecurity tools to help identify weaknesses in your applications, accessible on our Free Tools page.
Here’s a preview of our tool page:
 |
| Screenshot of Free Tools on Pentest Testing |
Example: SQL Injection Vulnerability Report
Using our free vulnerability assessment tool, you can generate detailed reports on your application’s security status. Here’s an example of a report for SQLi vulnerabilities:
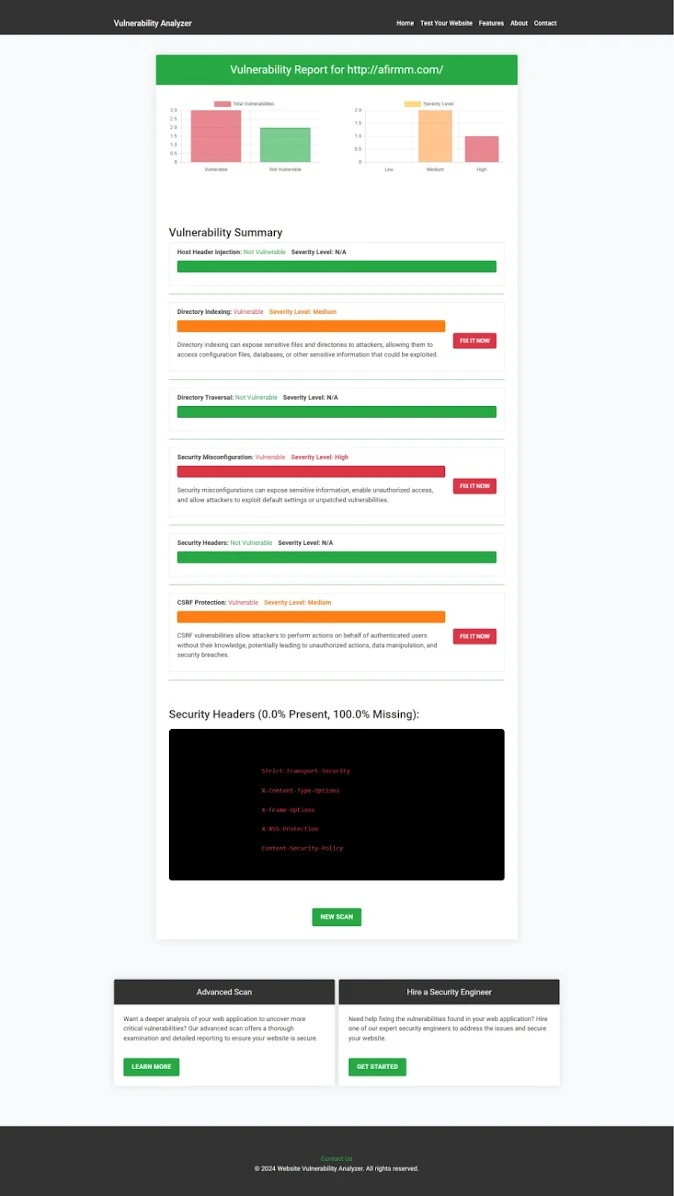 |
| Vulnerability Assessment Report Screenshot |
This report shows potential SQL Injection points and recommends steps for fixing them, helping you maintain a secure Symfony application.
More Cybersecurity Resources
Check out our additional resources for in-depth cybersecurity insights:
- Pentest Testing – Specializing in penetration testing and vulnerability analysis.
- Cyber Rely – Your go-to source for comprehensive cybersecurity services.
Conclusion
SQL Injection can have devastating effects on web applications, but by following secure coding practices, you can safeguard your Symfony applications. Use prepared statements, validate inputs, and regularly test your applications for vulnerabilities using our free tools.
This post provides foundational SQLi prevention tips and techniques for Symfony. We encourage you to explore our additional resources and stay proactive in cybersecurity.




Comments
Post a Comment