Fix Sensitive Data Exposure in Symfony Apps
Symfony is a powerful PHP framework known for its flexibility and robustness. But like any web technology, if it's not properly secured, it can become a target for attackers — especially when it comes to Sensitive Data Exposure. In this post, we’ll explore how this vulnerability occurs in Symfony applications and provide secure coding examples to mitigate the risk.
💡 Need to check your site for security vulnerabilities? Use our Free Website Vulnerability Scanner online today!
🔍 What is Sensitive Data Exposure?
Sensitive Data Exposure occurs when an application unintentionally exposes data such as:
-
Passwords
-
Credit card information
-
Session tokens
-
Personal Identifiable Information (PII)
In Symfony, this usually happens due to misconfigurations, improper error handling, or insecure data storage.
⚠️ Common Causes in Symfony
-
Exposing stack traces in production
-
Logging sensitive data (e.g., passwords or tokens)
-
Storing plain-text credentials
-
Weak encryption practices
-
Lack of HTTPS enforcement
🛠️ Coding Example 1: Improper Error Display
❌ Vulnerable Example
// config/packages/dev/monolog.yaml
monolog:
handlers:
main:
type: stream
path: "%kernel.logs_dir%/%kernel.environment%.log"
level: debug
This configuration might expose sensitive information if left in production.
✅ Fixed Example
// config/packages/prod/monolog.yaml
monolog:
handlers:
main:
type: stream
path: "%kernel.logs_dir%/prod.log"
level: error
Always restrict logging in production to avoid leaking stack traces and debug info.
🔒 Coding Example 2: Logging Sensitive Information
❌ Vulnerable Controller
public function login(Request $request)
{
$username = $request->get('username');
$password = $request->get('password');
$this->logger->info("Login attempt for: " . $username . " with password: " . $password);
}
✅ Secured Version
public function login(Request $request)
{
$username = $request->get('username');
$this->logger->info("Login attempt for: " . $username);
}
Never log passwords or any form of PII.
🔐 Coding Example 3: Encrypt Sensitive Data
When storing sensitive data, ensure it's encrypted before persisting it to the database.
✅ Secure Storing with Encryption
use Defuse\Crypto\Crypto;
use Defuse\Crypto\Key;
$key = Key::loadFromAsciiSafeString($_ENV['APP_SECRET']);
$encryptedData = Crypto::encrypt("Sensitive Info", $key);
// Save $encryptedData to database
✅ Decryption
$decryptedData = Crypto::decrypt($encryptedData, $key);
Make sure the APP_SECRET is securely stored and never hard-coded.
🛡️ Coding Example 4: Enforcing HTTPS
Always redirect HTTP traffic to HTTPS using Symfony’s secure headers.
# config/packages/framework.yaml
framework:
http_method_override: true
trusted_proxies: '%env(TRUSTED_PROXIES)%'
trusted_headers: ['x-forwarded-for', 'x-forwarded-proto']
# config/packages/security.yaml
firewalls:
main:
secure: true
🖼️ Screenshot 1: Our Website Vulnerability Scanner Tool
 |
| Screenshot of the free tools webpage where you can access security assessment tools. |
This tool scans your website for vulnerabilities — including Sensitive Data Exposure — with just one click.
🖼️ Screenshot 2: Vulnerability Assessment Report
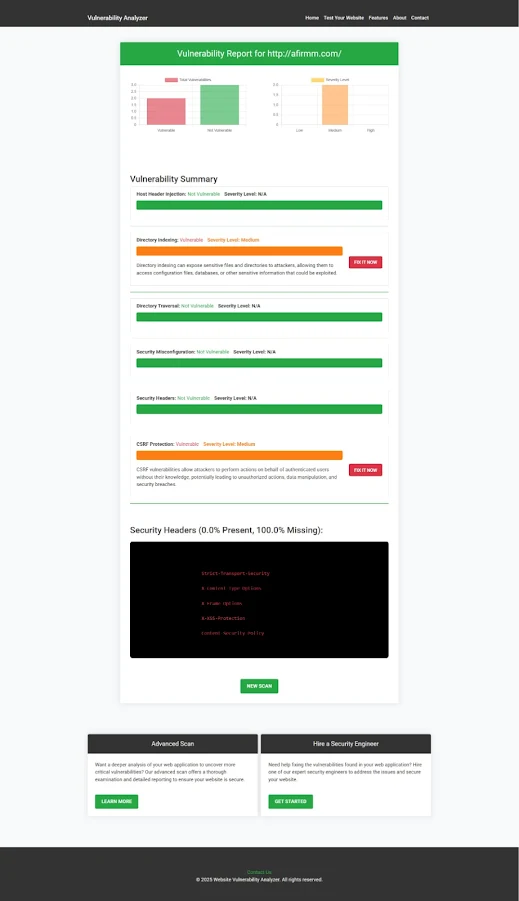 |
| An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities. |
Sample output from a recent scan showing a detailed summary of a website to check Website Vulnerability with misconfigured Symfony environment exposing data in dev mode.
🧩 Bonus: Best Practices to Avoid Sensitive Data Exposure
-
Set
APP_ENV=prodin production environments -
Store secrets using
.env.localor environment variables -
Use proper CORS configuration
-
Use strong password hashing algorithms like
bcryptorargon2i -
Regularly scan your Symfony app using tools like https://free.pentesttesting.com/
📢 Read More From Our Blog
Looking for more security tips and coding best practices? Visit our blog at Pentest Testing Corp.
🚀 Conclusion
Sensitive Data Exposure can compromise user trust and violate compliance standards like GDPR and PCI-DSS. Symfony developers must actively secure their applications by following secure coding practices, encrypting data, and limiting error reporting in production.
✅ Don’t forget to scan your Symfony app today using our free tool for a quick and free website security check.



Comments
Post a Comment