Fix Security Misconfiguration Issues in Symfony
Security misconfiguration is one of the most common yet critical vulnerabilities in modern web applications. Symfony, being a powerful PHP framework, offers many configuration options—but when misused or left insecure, it becomes a prime target for attackers.
In this blog post, we’ll explore how security misconfigurations can creep into Symfony applications, provide practical coding examples, and show you how to test your website using our Free Website Vulnerability Scanner online.
👉 Also check out more security tips on our blog at Pentest Testing Corp.
🔍 What is Security Misconfiguration?
Security misconfiguration refers to improperly configured security controls or settings in software or hardware systems. In Symfony, this can include:
-
Default configurations still active
-
Debug mode enabled in production
-
Insecure HTTP headers
-
Overly verbose error messages
-
Unprotected files and directories
-
Unrestricted administrative panels
Misconfigurations can give hackers the exact clues they need to exploit your system.
🧪 Real-World Example 1: Debug Mode Left On
Vulnerability:
If your .env file or APP_ENV variable is set to dev or test in production, Symfony may expose sensitive stack traces.
Code Example:
# Vulnerable Configuration
APP_ENV=dev
APP_DEBUG=1
Fix:
# Secure Configuration
APP_ENV=prod
APP_DEBUG=0
Always make sure your APP_ENV is set to prod in production.
🔐 Real-World Example 2: Insecure HTTP Headers
Symfony doesn’t send all secure headers by default. Missing headers like X-Frame-Options, X-XSS-Protection, and Strict-Transport-Security can open up your app to attacks.
Add Secure Headers in Symfony:
# config/packages/framework.yaml
framework:
http_method_override: true
trusted_proxies: ~
trusted_headers: [ "x-forwarded-for", "x-forwarded-proto" ]
# config/packages/security.yaml
security:
firewalls:
main:
headers:
x_frame_options: DENY
x_content_type_options: nosniff
x_xss_protection: "1; mode=block"
These configurations help reduce risks of Clickjacking, MIME sniffing, and XSS.
🚫 Real-World Example 3: Directory Listings Enabled
Accidentally exposing directories such as /var, /vendor, or /config can be a huge risk.
Ensure .htaccess is configured to block access:
# public/.htaccess
<Directory "/var">
Order allow,deny
Deny from all
</Directory>
Or better yet, move sensitive directories outside the web root.
💣 Real-World Example 4: Default Admin Route Exposed
Many Symfony applications expose admin routes such as /admin, which are easy to guess.
Fix:
-
Rename routes
-
Add IP whitelisting
-
Enforce multi-factor authentication (MFA)
# config/routes.yaml
admin_area:
path: /secure-admin-9d3f
controller: App\Controller\AdminController::dashboard
🛡 Scan Your Symfony App for Security Misconfigurations
You don’t need to guess whether your app is secure—run a Website Security check for free using our online tool.
📸 Screenshot: Free Website Security Checker
 |
| Screenshot of the free tools webpage where you can access security assessment tools. |
📊 Vulnerability Report: Real Scan Result
Once your scan completes, you’ll get a detailed vulnerability assessment report to check Website Vulnerability outlining the weaknesses in your Symfony application.
📸 Screenshot: Sample Vulnerability Assessment Report
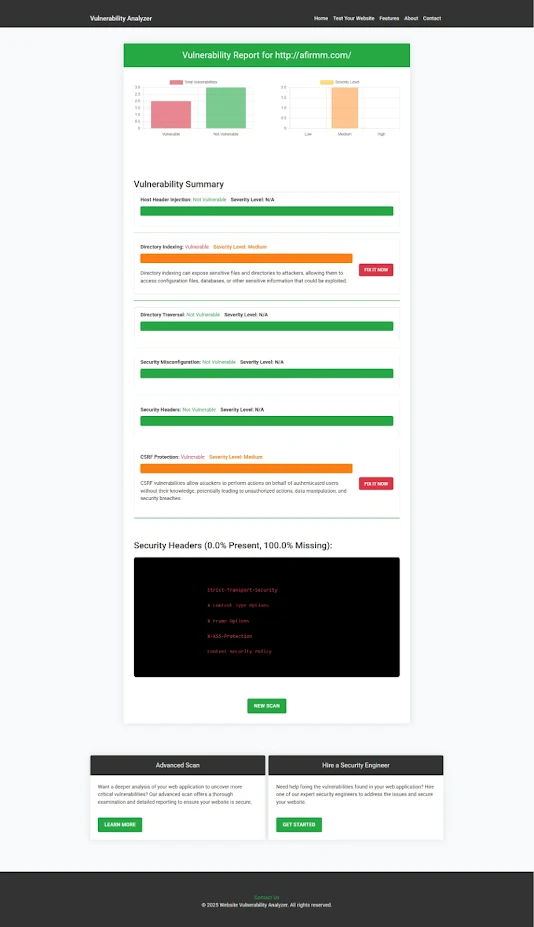 |
| An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities. |
🔄 Final Thoughts
Security misconfiguration in Symfony can leave your application wide open to attackers—but with careful attention to configuration files, headers, and environment variables, you can lock it down effectively.
Regular vulnerability scanning is essential. You can use our Free Website Security Scanner to ensure your app is safe and secure.
For more practical web security blogs, visit us at 👉 Pentest Testing Corp. Blog.
🧠 Key Takeaways:
-
Never run production systems in debug mode.
-
Secure your HTTP headers manually.
-
Hide sensitive files and rename common admin paths.
-
Use automated tools for continuous vulnerability scanning.
Let us know your thoughts in the comments below, and don’t forget to share this post if you found it helpful!



Comments
Post a Comment