Prevent Remote Code Execution (RCE) Vulnerabilities in Symfony
Introduction
Remote Code Execution (RCE) vulnerabilities are a critical security risk for any web application, and Symfony-based applications are no exception. RCE allows attackers to execute arbitrary code on the server, potentially leading to severe data breaches, system compromises, or full server control. In this post, we’ll explore how RCE vulnerabilities manifest in Symfony, how to prevent them and share practical coding examples.
By the end of this article, you’ll have a better understanding of securing Symfony applications against these attacks and using our Website Vulnerability Scanner tool to check for vulnerabilities in your web apps.
What is Remote Code Execution (RCE)?
Remote Code Execution (RCE) is a type of vulnerability that allows an attacker to run arbitrary code on a target system. This is typically achieved by exploiting flaws in the application that allow user input to be executed as code on the server. In Symfony, common RCE vulnerabilities arise from poor validation of user inputs or improper handling of external libraries.
Common Causes of RCE Vulnerabilities in Symfony
-
Unvalidated User Input: If user input is directly passed to functions that execute code, attackers can inject malicious payloads.
-
Improper Use of Symfony Components: Components like the
exec()function or certain commands in Symfony may unintentionally allow the execution of untrusted code if improperly sanitized. -
Misconfigured Permissions: An application might allow users to upload files or execute commands with improper permissions, leading to RCE.
-
Outdated Dependencies: Running outdated libraries and packages in your Symfony application can introduce vulnerabilities that are already known to the attacker community.
How to Prevent RCE Vulnerabilities in Symfony
1. Sanitize and Validate User Inputs
Always validate user inputs and sanitize them before they are passed to functions like eval(), exec(), or other similar functions. For example:
// Avoid directly executing user input
$userInput = $_GET['command'];
// Dangerous: eval($userInput);
// Instead, sanitize and validate the input
if (preg_match('/^[a-zA-Z0-9_]+$/', $userInput)) {
// Safe to execute the command
$output = shell_exec($userInput);
} else {
// Invalid input
echo "Invalid input!";
}
Explanation: The code above ensures that only alphanumeric characters and underscores are allowed in the user input, significantly reducing the risk of RCE.
2. Use Symfony’s Built-in Security Features
Symfony offers robust security features like user authentication, role management, and access control. By enforcing proper user authentication and roles, you can restrict access to potentially dangerous actions.
# In your security.yaml
firewalls:
secure_area:
pattern: ^/admin
guard:
authenticator: App\Security\LoginAuthenticator
Explanation: By securing sensitive routes with authentication, you can prevent unauthorized access to functions that could be exploited for RCE attacks.
3. Keep Symfony and Dependencies Updated
Always ensure that your Symfony framework and its dependencies are up-to-date. This will minimize the chances of known vulnerabilities being present in your application.
# Use Composer to update your Symfony packages
composer update
4. Limit File Uploads and Permissions
If your application allows file uploads, make sure you validate file types and enforce strict file size limits. Also, restrict where files can be stored to avoid unwanted access to critical parts of your server.
if ($_FILES['uploaded_file']['type'] !== 'image/jpeg') {
echo "Only JPEG images are allowed.";
exit;
}
// Further checks can be implemented to ensure the file is safe to handle
Testing for RCE Vulnerabilities Using Our Free Tool
To ensure that your Symfony application is free from Remote Code Execution vulnerabilities, you can use our free Website Vulnerability Scanner online. This tool scans your website and provides a comprehensive vulnerability assessment.
Here’s a screenshot of our tool in action:
 |
| Screenshot of the free tools webpage where you can access security assessment tools. |
The vulnerability assessment report generated can help you identify and mitigate RCE risks in your Symfony application.
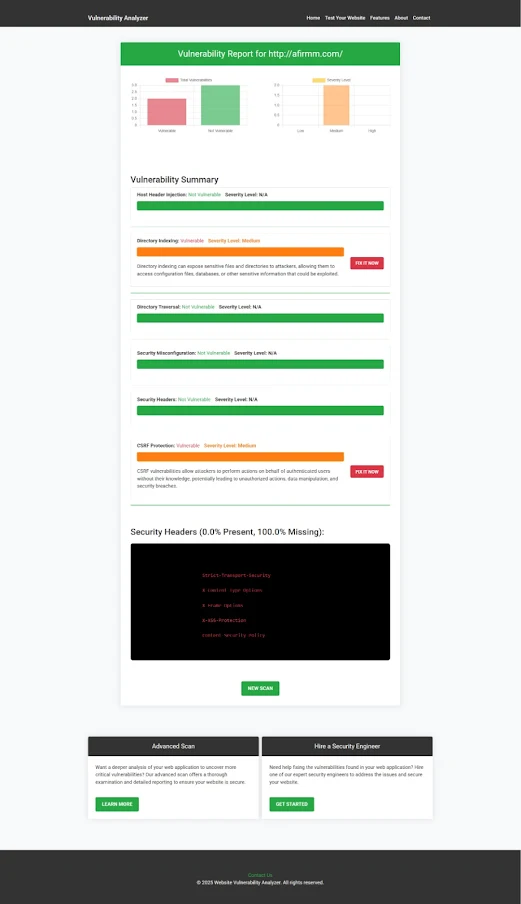 |
| An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities. |
How to Conduct Web App Penetration Testing
Penetration testing is crucial for uncovering vulnerabilities like RCE. At Pentest Testing Corp, we offer professional web app penetration testing services to help you identify weaknesses in your application before they can be exploited.
We use a combination of automated tools and manual testing to conduct thorough assessments, ensuring all vulnerabilities are caught.
For more information, visit our Web App Penetration Testing Services page.
Conclusion
Remote Code Execution vulnerabilities are critical to address in any web application, especially when using frameworks like Symfony. By following the guidelines mentioned above and using the free tool for Website Security checks, you can significantly reduce the risk of these attacks. Regular testing and secure coding practices are essential to keeping your application safe.
If you have any questions or need further assistance, feel free to check out our Pentest Testing Blog for more insightful posts.
%20in%20Symfony%20%7C%20Full%20Guide.jpg)



Comments
Post a Comment