Prevent IDOR Vulnerabilities in Laravel: A Quick Guide
What is IDOR in Laravel?
Insecure Direct Object References (IDOR) is a common web vulnerability where unauthorized users access sensitive data or functionality by manipulating object references. This vulnerability is especially critical in Laravel applications, where robust security measures are a must to safeguard against unauthorized access.
In this post, we’ll explore IDOR in Laravel, provide a coding example to demonstrate how it occurs, and show how you can detect such vulnerabilities using our free Website Security Checker.
Understanding IDOR with an Example
Imagine you have an e-commerce platform built with Laravel where users can view their order details through a URL like this:
If the application doesn't validate user permissions properly, attackers could change the ID in the URL to view someone else’s order:
This is a classic IDOR vulnerability that can lead to serious data breaches.
How to Prevent IDOR in Laravel
To prevent IDOR in Laravel, always implement proper authorization checks. Here’s an example:
This code ensures that only the order's owner can view it.
Visualize Security with Free Tools
To identify vulnerabilities like IDOR in your Laravel application, use our Free Website Security Checker Tool. Here’s a snapshot of the tool interface:
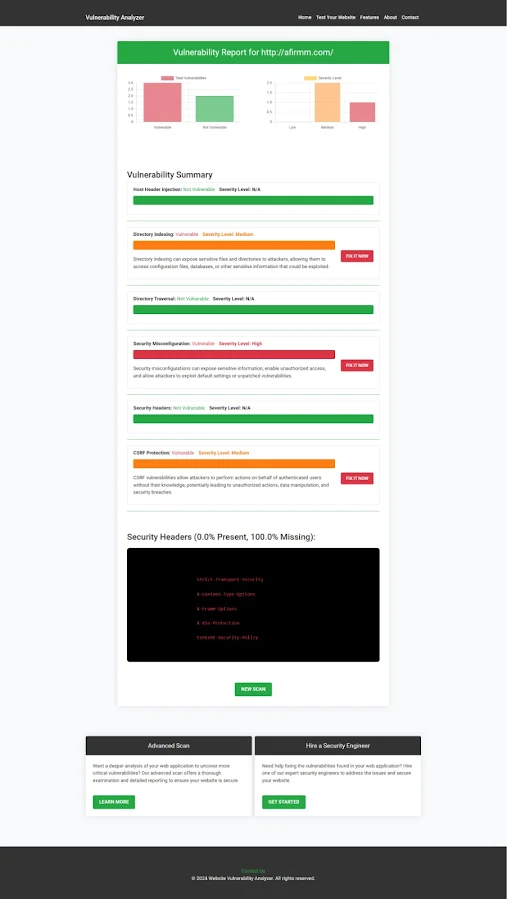
Detecting and Reporting Vulnerabilities
Once you’ve run a scan with our free tool, you'll receive a detailed Vulnerability Assessment Report, like the one shown below:
Conclusion: Take Action Against IDOR
Securing your Laravel applications against IDOR is crucial to protecting sensitive data and building user trust. By following the coding practices outlined in this blog and leveraging tools like our Free Website Security Checker, you can proactively safeguard your applications.
Don’t let IDOR leave your system vulnerable. Scan your website today and stay one step ahead of potential threats!
%20in%C2%A0Laravel.jpg)



Comments
Post a Comment