Protecting WordPress Site from SQL Injection (SQLi) Attacks
How to Secure WordPress Site Against SQL Injection (SQLi)
WordPress powers a significant portion of the internet, making it a prime target for SQL Injection (SQLi) attacks. SQLi vulnerabilities can allow attackers to gain unauthorized access, steal sensitive data, and, in extreme cases, take control of the site entirely. This post breaks down what SQLi is, provides a vulnerable coding example, and highlights effective security steps to keep your WordPress site safe.
%20Attacks.jpg) |
What is SQL Injection, and Why is it a Threat to WordPress?
SQL Injection occurs when attackers exploit weak SQL queries by injecting malicious code into input fields or URLs. WordPress, with its MySQL dependency, can be at risk for SQLi attacks, especially if plugins or themes aren’t securely coded.
Let’s look at a common example of vulnerable code:
If a malicious user inputs ' OR 1=1 -- as the username, the query could return true, bypassing the password check and potentially exposing your site to unauthorized access.
How to Protect Your WordPress Site from SQL Injection
The best way to guard against SQL injection is by using prepared statements and parameterized queries. These methods ensure that input data is properly sanitized and prevent SQL injection attacks.
Example of Secure Code in WordPress:
In this secure code, $wpdb->prepare prevents SQL injection by binding variables, ensuring they’re properly formatted before interacting with the database.
Additional Tips to Prevent SQL Injection in WordPress
- Sanitize Inputs: Use WordPress sanitization functions like
sanitize_text_field()andesc_sql()for all data that interacts with the database. - Limit Permissions: Only provide necessary database permissions. For example, avoid using root privileges for your WordPress database user.
- Use Secure Plugins and Themes: Be selective about the plugins and themes you use, ensuring they are from reputable sources with security updates.
Screenshot Guide to Free Security Tools and Vulnerability Report
 |
| Screenshot of Free Website Vulnerability Scanner tool on Pentest Testing Corp. |
To ensure your WordPress site is safe from SQLi and other vulnerabilities, consider using our Free Website Vulnerability Scanner Tools. These tools are designed to help you quickly assess and improve your site's security posture.
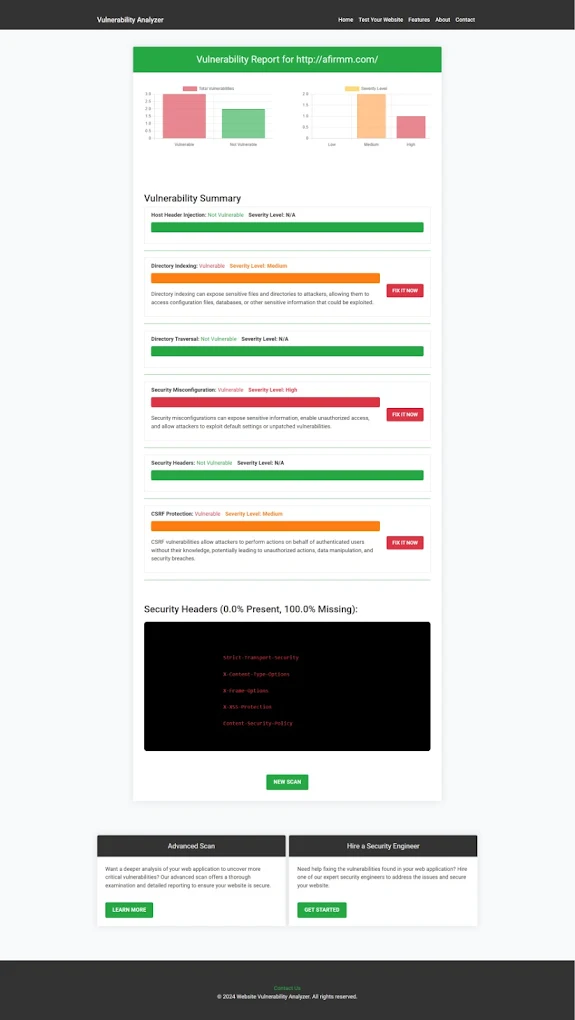 |
| Vulnerability Assessment Report Screenshot by Pentest Testing Corp.'s Free Website Vulnerability Checker tool |
Here’s a sample Vulnerability Assessment Report that identifies potential weaknesses, including SQLi risks. Run a scan with our tools to safeguard your WordPress site.
Explore More at Cyber Rely and Pentest Testing
For more guidance on WordPress security, check out our resources on the Cyber Security blog. We also recommend PentestTesting, where you’ll find expert advice on securing WordPress and other platforms against SQLi and similar threats.
By following these security practices and regularly assessing your site, you can protect your WordPress site from SQL Injection threats. Remember, a secure site builds trust with your visitors and keeps your data safe!



Comments
Post a Comment