SQL Injection (SQLi) in RESTful APIs: Detection & Prevention
Understanding SQL Injection (SQLi) in RESTful APIs
With the increasing reliance on RESTful APIs in modern applications, attackers have shifted their focus to exploiting vulnerabilities in APIs. One of the most common threats is SQL Injection (SQLi), where malicious SQL statements are injected into an input field to manipulate or gain unauthorized access to a database.
In this blog, we’ll explain how SQL Injection works in RESTful APIs, provide a coding example, and demonstrate how to use tools like our free Website Security Checker to detect such vulnerabilities.
What is SQL Injection in RESTful APIs?
SQL Injection is a type of attack where an attacker exploits the way SQL queries are handled in an application. APIs are especially vulnerable if they:
- Accept user input directly without proper sanitization.
- Dynamically construct SQL queries using input parameters.
SQL Injection in Action: A Coding Example
Here’s a basic example of a vulnerable RESTful API endpoint:
Vulnerable Code Example:
How an Attacker Exploits It:
An attacker could pass username=admin' OR '1'='1 as a query parameter. This manipulates the SQL query to always return all rows from the database.
How to Prevent SQL Injection in RESTful APIs
Use Parameterized Queries:
Avoid string interpolation in SQL queries. Use parameterized queries to handle user input safely.Secure Code Example:
Input Validation:
Validate and sanitize all user inputs before processing them.Use ORM Libraries:
Object-Relational Mapping (ORM) tools like SQLAlchemy can abstract SQL queries and reduce the risk of injection attacks.Monitor with Security Tools:
Use vulnerability scanners like our Website Security Checker to detect SQL Injection vulnerabilities in your APIs.
Testing APIs for Vulnerabilities
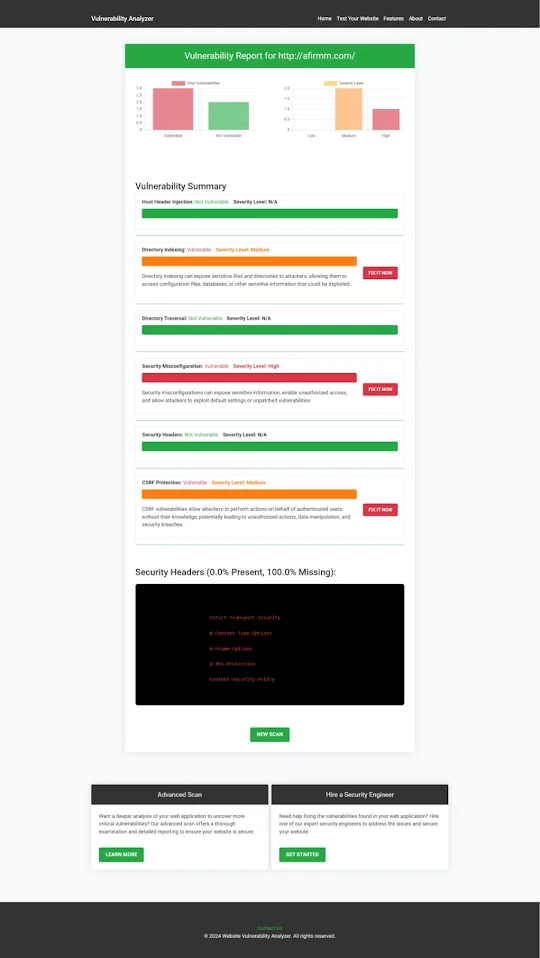
Here’s how you can use our free tool to assess your APIs for SQL Injection vulnerabilities:
Step 1: Visit Our Free Tool
Open Website Security Checker. Enter your API endpoint URL and start the vulnerability assessment.
Step 2: Review the Report
Once the scan is complete, download the vulnerability report. The report will highlight SQL Injection risks and other vulnerabilities.
Why Focus on SQL Injection in RESTful APIs?
APIs are critical to application functionality and are often exposed to the internet. This makes them prime targets for attackers. By securing your APIs against SQL Injection, you not only protect your data but also enhance the trust of your users and stakeholders.
Conclusion
SQL Injection attacks in RESTful APIs can lead to severe consequences, including data breaches and unauthorized access. By following best practices like parameterized queries and using tools like Website Security Checker, you can proactively secure your APIs.
Start securing your APIs today! Check your website for vulnerabilities with our free tool now.
Call to Action:
Share this blog with your developer community to spread awareness about securing RESTful APIs against SQL Injection!
%20in%20RESTful%20APIs.jpg)




Comments
Post a Comment