Fix Security Misconfigurations in Laravel (Step-by-Step Guide)
Understanding Security Misconfigurations in Laravel
Security misconfiguration is one of the most common vulnerabilities affecting web applications today. It often stems from improperly configured servers, frameworks, or applications. Laravel, being a popular PHP framework, is no exception and can be susceptible to such issues if not properly secured.
In this blog, we’ll explore common security misconfigurations in Laravel, demonstrate how to fix them and show how you can use our free Website Security Checker tool to identify vulnerabilities in your Laravel applications.
What Are Security Misconfigurations?
Security misconfiguration occurs when default settings, incomplete configurations, or exposed sensitive information make an application vulnerable. Examples in Laravel include:
- Leaving
debugmode enabled in production. - Exposing sensitive
.envfiles. - Improper access control.
Common Laravel Security Misconfigurations and Fixes
1. Debug Mode Enabled in Production
Leaving debug mode on in a production environment exposes sensitive application data, which can be exploited by attackers.
Solution:
Ensure the APP_DEBUG value is set to false in the .env file:
env
APP_DEBUG=false
To apply this configuration, run:
bash
php artisan config:cache
2. Exposed .env Files
The .env file contains sensitive information like database credentials and API keys. If exposed, it can lead to unauthorized access.
Solution:
Add the following rule in your .htaccess file to prevent .env files from being publicly accessible:
apache
<Files .env>
Order allow,deny
Deny from all
</Files>
3. Insecure Directory Permissions
Incorrect permissions on directories can allow attackers to modify files or access sensitive data.
Solution:
Set proper permissions for your Laravel project:
- Set the
storageandbootstrap/cachedirectories to775. - Other files and directories should be set to
644or755as needed.
chmod -R 775 storage bootstrap/cache
chmod -R 644 other_directories
Enhance Your Laravel Security with Our Free Tool
You can easily check your website for security misconfigurations using our Website Security Scanner tool.
Screenshot:
 |
| Our free tool detects misconfigurations and offers suggestions to improve your Laravel application’s security. |
A Coding Example: Securing Route Middleware
Laravel routes can be secured using middleware to ensure only authorized users can access specific endpoints.
Example:
php// In your routes/web.php file Route::get('/admin', [AdminController::class, 'index'])->middleware('auth');
Ensure the auth middleware is properly configured to redirect unauthenticated users:
// In app/Http/Middleware/Authenticate.php
public function handle($request, Closure $next) {
if (!auth()->check()) {
return redirect('/login');
}
return $next($request);
}
This setup ensures that only logged-in users can access the /admin route.
Sample Report from Our Security Tool
Here’s an example of a vulnerability assessment report generated using our Website Security Checker tool:
Screenshot:
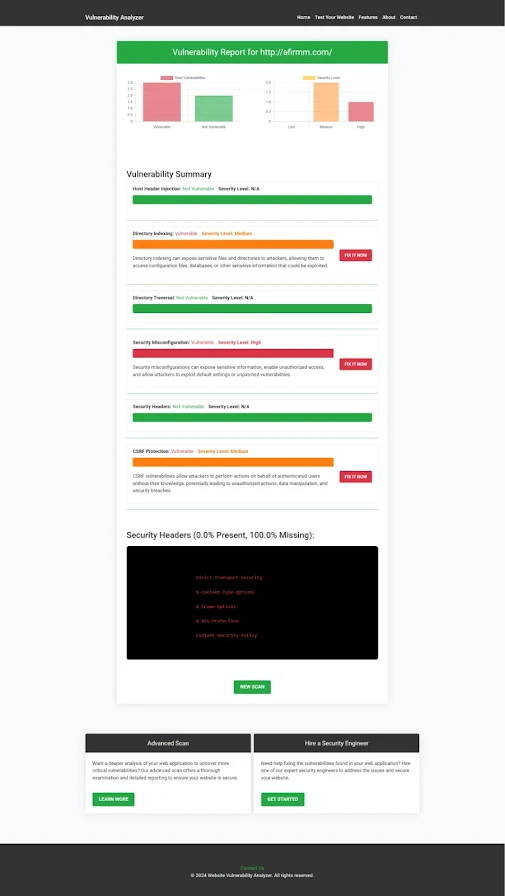 |
| The report highlights identified security misconfigurations and actionable recommendations. |
Conclusion
Securing your Laravel application from misconfigurations is critical to prevent exploitation. By following best practices, implementing proper configurations, and using tools like our Website Security Checker, you can safeguard your application effectively.
Start by analyzing your website for vulnerabilities today and take proactive measures to strengthen your security!




Comments
Post a Comment