How to Prevent CSP Bypass in Laravel: A Comprehensive Guide
Introduction
Content Security Policy (CSP) is a critical security feature that helps protect websites from various attacks, including Cross-Site Scripting (XSS) and data injection. However, misconfigurations or bypass vulnerabilities in CSP can still lead to security risks in Laravel applications.
In this blog post, we'll explore common methods attackers use to bypass CSP and how you can harden your Laravel application to prevent these vulnerabilities.
What is CSP?
CSP is a browser feature that helps prevent the execution of malicious scripts on web pages. By defining a policy for where resources can be loaded, CSP can significantly reduce the risk of XSS attacks.
In Laravel, CSP can be configured in a middleware to control resource loading. However, if not configured properly, attackers can bypass CSP and inject malicious content into your application.
Common CSP Bypass Techniques
1. Use of ‘unsafe-inline’ in CSP
A common mistake when setting up CSP in Laravel is including 'unsafe-inline' in the policy. This directive allows the execution of inline JavaScript, which can be exploited by attackers to inject malicious code.
Example:
Header set Content-Security-Policy "default-src 'self'; script-src 'self' 'unsafe-inline';"
Solution: Avoid using 'unsafe-inline'. If you absolutely must use inline scripts, make sure to implement a nonce or hash-based CSP.
Header set Content-Security-Policy "default-src 'self'; script-src 'self' 'nonce-<random_nonce>'"
By using nonces, the script execution is restricted to those that are explicitly authorized, reducing the attack surface.
2. Allowing ‘data:’ URIs
Allowing 'data:' URIs in CSP can lead to vulnerabilities, especially in scenarios where base64-encoded payloads can be injected into your website.
Example:
Header set Content-Security-Policy "default-src 'self'; img-src 'self' data:;"
Solution: Restrict 'data:' URIs for images and other media types to prevent attackers from injecting malicious content via data URIs.
Header set Content-Security-Policy "default-src 'self'; img-src 'self';"
3. Exposing URL Parameters
Attackers can bypass CSP by exploiting URL parameters. By passing malicious script payloads through query strings or fragment identifiers, they may be able to execute harmful code.
Example:
// This allows attackers to inject malicious JavaScript via URL parameters.
Header set Content-Security-Policy "default-src 'self'; script-src 'self' http://example.com;"
Solution: Sanitize URL parameters and avoid reflecting them in JavaScript contexts.
// Proper sanitization before reflecting URL parameters
$clean_input = htmlspecialchars($_GET['input'], ENT_QUOTES, 'UTF-8');
Setting Up CSP in Laravel
Laravel makes it easy to integrate CSP by using middleware. Here's how you can set up CSP headers in your application.
Step 1: Create a Middleware
Run the following Artisan command to create a custom middleware:
php artisan make:middleware ContentSecurityPolicy
Step 2: Define CSP in Middleware
Edit the generated middleware file located in app/Http/Middleware/ContentSecurityPolicy.php:
namespace App\Http\Middleware;
use Closure;
use Illuminate\Http\Request;
class ContentSecurityPolicy
{
public function handle(Request $request, Closure $next)
{
$response = $next($request);
$csp = "default-src 'self'; script-src 'self' 'nonce-".base64_encode(random_bytes(32))."';";
$response->headers->set('Content-Security-Policy', $csp);
return $response;
}
}
This middleware generates a nonce for each request and sets the appropriate CSP header to prevent inline script execution.
Step 3: Register Middleware
Next, register the middleware in your app/Http/Kernel.php:
protected $middleware = [
// Other middlewares...
\App\Http\Middleware\ContentSecurityPolicy::class,
];
Testing Your CSP Policy
Once you've implemented your CSP headers, it's crucial to test whether they're functioning as expected.
Use our Website Vulnerability Scanner tool to assess the CSP configuration of your Laravel app.
 |
| Screenshot of the free tools webpage where you can access security assessment tools to check Website Vulnerability. |
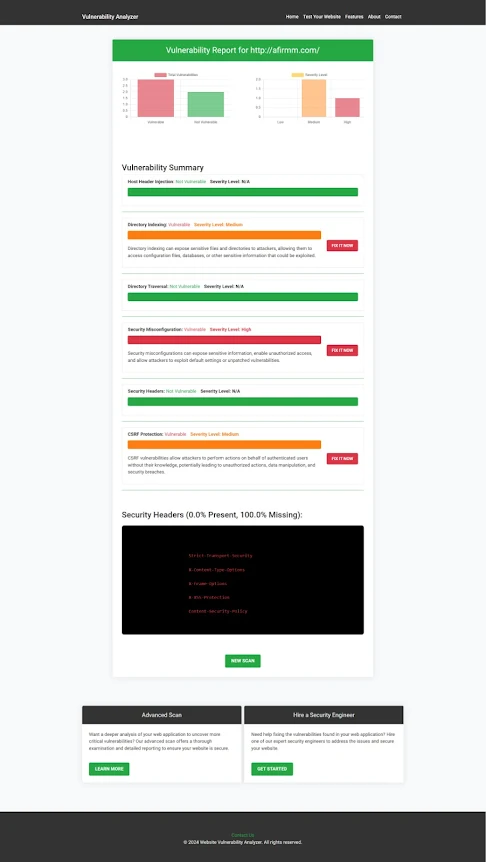 |
| An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities. |
Conclusion
Securing your Laravel application against CSP bypass attacks is crucial for maintaining the integrity of your website and protecting your users from malicious scripts. By carefully configuring your CSP headers and following the steps outlined in this post, you can significantly reduce the risk of these vulnerabilities.
For more tips on securing your web applications, check out our blog at Pentest Testing Blog.
By keeping your security policies tight and continuously testing your application, you’ll be one step ahead in the battle against malicious attacks.
%20in%C2%A0Laravel.jpg)



Comments
Post a Comment