How to Prevent Web Cache Deception in Laravel
Introduction
A Web Cache Deception (WCD) attack occurs when an attacker manipulates the cache behavior of your application to serve sensitive data publicly. In Laravel, a powerful PHP framework, it's crucial to secure your application against such attacks to ensure that sensitive information isn’t cached and served to unauthorized users.
In this post, we'll explore how web cache deception works, how it can be prevented, and how code can be implemented to secure your Laravel app. Plus, we will show you how to use our free website security scanner tool to assess your website for security vulnerabilities.
What is a Web Cache Deception Attack?
Web Cache Deception is an attack where the attacker tricks your caching mechanism into caching sensitive data that should not be publicly accessible. This can lead to the exposure of user-specific data, session information, or even backend logic that is not intended to be accessed by unauthorized users.
For example, an attacker might try to access a cached page that appears to be public but is actually storing sensitive data, such as user profiles, admin panels, or even private dashboards.
How Web Cache Deception Works
In Laravel, cache management can be complex due to the use of tools like HTTP Cache, Memcached, or Redis. When improper configurations are made, sensitive pages may inadvertently be cached and then served to unauthorized users. Here's a simple illustration of how a WCD attack can occur:
- An attacker accesses a dynamic page (e.g.,
http://example.com/dashboard) but modifies the URL to something seemingly static, likehttp://example.com/dashboard/. - Laravel’s cache mechanism may store this page as static content, thinking it is public.
- The attacker later accesses the cached version, which contains sensitive information meant for the original user.
How to Prevent Web Cache Deception Attacks in Laravel
Preventing WCD attacks involves a few key strategies:
-
Avoid Caching Sensitive Pages:
The most important step is to avoid caching pages that contain sensitive data. If you're caching pages in Laravel, ensure that only public-facing pages are cached.
Example:Route::get('/user/{id}', 'UserController@show')->middleware('noCache'); -
Use Cache-Control Headers Properly:
Make sure that Cache-Control headers are correctly set for pages that should not be cached. Example:return response()->view('dashboard') ->header('Cache-Control', 'no-store, no-cache, must-revalidate, proxy-revalidate'); -
Secure Cache Key Generation:
Make sure that your cache keys are generated uniquely for each user session. This will ensure that a user-specific cache isn’t used by someone else. Example:$cacheKey = 'user_dashboard_' . auth()->id(); Cache::remember($cacheKey, $minutes, function() { return view('dashboard'); }); -
Ensure Dynamic Content Isn't Cached:
For dynamic content that varies depending on the user, make sure caching is bypassed. Example:if (auth()->check()) { return response('This is your personal dashboard'); }
Using Our Free Website Security Checker
Before implementing these strategies, it's always a good idea to check the security status of your website. You can use our free Website Security Checker to perform a thorough security assessment.
Here's a screenshot of how our website security tool looks:
 |
| Screenshot of the free tools webpage where you can access security assessment tools. |
After running the check for a Website Security test, you'll receive a detailed report of any vulnerabilities, including cache-related issues. Here's an example of a vulnerability assessment report that identifies potential cache misconfigurations:
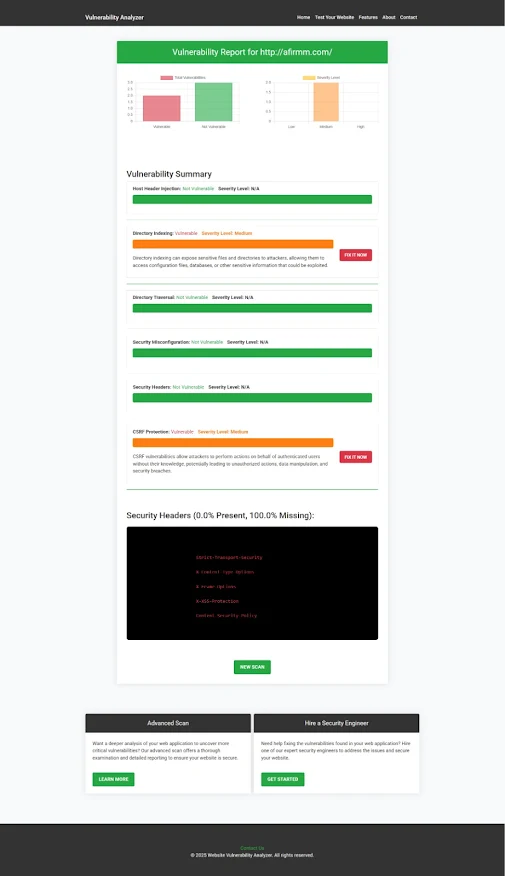 |
| An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities. |
Conclusion
Web Cache Deception is a serious threat to your Laravel applications, but with the proper precautions, you can easily mitigate the risks. By following the steps mentioned above and using tools like ours to check Website Vulnerability, you can ensure your application is secure.
For more insights into securing Laravel applications, check out our blog on Pentest Testing Corp.




Comments
Post a Comment