Prevent Session Replay Attacks in Laravel: A Complete Guide
Introduction
Session replay attacks are a serious security concern in web applications, including Laravel-based projects. In these attacks, a malicious actor intercepts and replays a legitimate user's session to gain unauthorized access to sensitive data or perform malicious actions. This blog will walk you through what session replay attacks are, why they occur, and how to effectively prevent them in Laravel applications.
What is a Session Replay Attack?
A session replay attack occurs when an attacker intercepts a session token (like a cookie or authentication token) and replays it to impersonate the legitimate user. This type of attack can bypass authentication mechanisms and allow attackers to access user accounts without needing to know login credentials.
How to Prevent Session Replay Attacks in Laravel
To safeguard your Laravel application from session replay attacks, you need to implement multiple strategies to ensure that session tokens cannot be reused maliciously.
1. Use Secure and HttpOnly Cookies
One of the simplest ways to defend against session replay attacks is by securing your session cookies. Laravel makes this easy by setting secure and HttpOnly flags in the session configuration.
In config/session.php, ensure you have these settings:
'secure' => env('SESSION_SECURE_COOKIE', true), // Set to true if using HTTPS
'http_only' => true, // Prevent client-side access to session cookie
This ensures that cookies are only sent over HTTPS and cannot be accessed through JavaScript, reducing the risk of interception by malicious scripts.
2. Implement Session Expiry and Regeneration
To mitigate the risk of session reuse, it's essential to regenerate the session ID periodically and set reasonable session expiration times. Laravel has built-in support for session expiration in config/session.php:
'lifetime' => 120, // Session expires after 120 minutes
'expire_on_close' => true, // Expire session on browser close
Additionally, you can regenerate the session ID on login or after a certain period of time:
public function regenerateSession()
{
session()->regenerate();
}
This ensures that even if an attacker intercepts a session token, it will no longer be valid after the session is regenerated.
3. Token-Based Authentication with Laravel Passport
Another powerful way to prevent session replay attacks is by using token-based authentication, such as Laravel Passport. This method avoids traditional session management by using stateless tokens for authentication, making it more difficult for attackers to intercept valid session data.
Here’s an example of using Passport in Laravel:
use Laravel\Passport\HasApiTokens;
class User extends Authenticatable
{
use HasApiTokens;
}
By issuing tokens and validating them via API requests, you reduce the risk of session token interception and replay.
4. Implement CSRF Protection
Cross-Site Request Forgery (CSRF) protection ensures that every form submission and state-changing request is genuine. Laravel includes CSRF protection out of the box, but you should always ensure that the token is properly included in forms:
<form method="POST" action="/submit-form">
@csrf
<!-- Other form fields -->
</form>
This protects against unauthorized requests, including those replayed by attackers using stolen session tokens.
5. Monitor and Log Suspicious Activities
You can also integrate logging and monitoring to detect suspicious login patterns or repeated failed attempts. Laravel makes logging easy with the Log facade:
use Illuminate\Support\Facades\Log;
Log::warning('Suspicious login attempt detected for user: ' . $user->email);
By tracking abnormal login activity, you can identify possible session replay attempts and respond proactively.
Adding a Security Layer: Using Pentest Testing's Free Website Security Checker
To further enhance the security of your Laravel application, we recommend using the website vulnerability scanner tool. This tool will scan your website for vulnerabilities, including session-related issues, and help you address potential weaknesses that could be exploited in session replay attacks.
Image 1: Screenshot of the Webpage of Our Free Tool
 |
| Screenshot of the free tools webpage where you can access security assessment tools. |
You can see the free security scanner tool in action, helping you ensure that your website is protected against session replay and other security threats.
Conclusion
Session replay attacks can be a severe threat to web applications, but with the right precautions, you can effectively safeguard your Laravel project. By following best practices such as secure cookie handling, session regeneration, token-based authentication, and CSRF protection, you can significantly reduce the risk of such attacks.
For even more comprehensive security, make sure to run regular vulnerability assessments using tools like the free website security scanner tool.
Image 2: Screenshot of a Website Vulnerability Assessment Report.
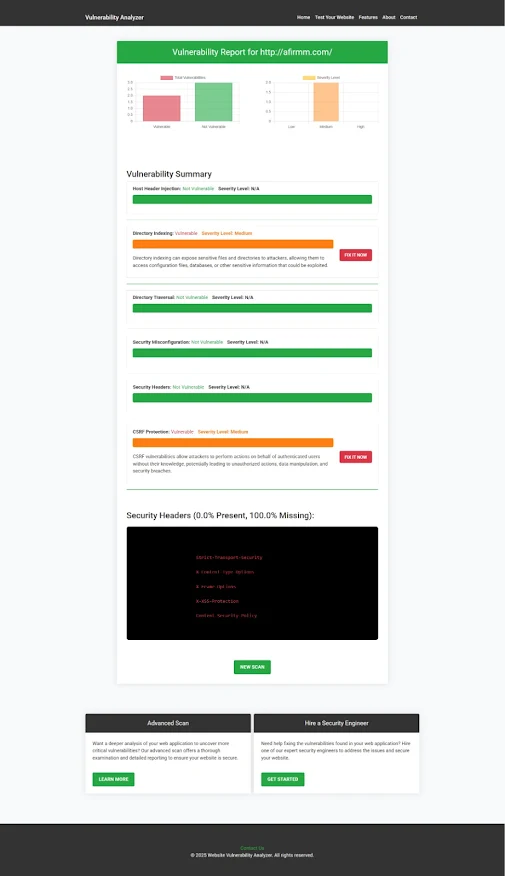 |
| An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities. |
This report demonstrates the value of using our tool for a website security test to identify and resolve vulnerabilities before they can be exploited by attackers.
For more insights on web security, check out our blog at Pentest Testing Corp.




Comments
Post a Comment