Fix Broken Access Control in Symfony Securely
Broken Access Control is one of the most critical vulnerabilities in web applications today, and yes—Symfony-based applications are no exception. Insecure permission logic, missing role checks, or insecure direct object references can lead to unauthorized data access, account takeover, or privilege escalation.
In this post, we’ll explore real-world examples of Broken Access Control in Symfony applications, demonstrate how attackers exploit them, and provide secure coding practices. All examples are practical and easily testable with our free Website Vulnerability Scanner online tool.
🚨 What Is Broken Access Control?
Broken Access Control occurs when users can act outside their intended permissions. For instance, a normal user accessing an admin dashboard or modifying another user’s data just by changing a URL parameter.
Symfony makes it relatively easy to manage access rules, but if those configurations are overlooked or bypassed through insecure code, it creates a high-risk vulnerability.
🔍 Example 1: Role-Based Access Not Enforced
Consider this controller in Symfony:
// src/Controller/AdminController.php
use Symfony\Bundle\FrameworkBundle\Controller\AbstractController;
use Symfony\Component\Routing\Annotation\Route;
class AdminController extends AbstractController
{
/**
* @Route("/admin", name="admin_dashboard")
*/
public function index()
{
return $this->render('admin/dashboard.html.twig');
}
}
In this example, no access control is applied. Anyone can access /admin, including unauthenticated users. Here's how to fix it:
// Secured version with role check
/**
* @Route("/admin", name="admin_dashboard")
*/
public function index()
{
$this->denyAccessUnlessGranted('ROLE_ADMIN');
return $this->render('admin/dashboard.html.twig');
}
This ensures only users with ROLE_ADMIN can access the admin dashboard.
🔐 Example 2: Insecure Direct Object Reference (IDOR)
Let’s say you have this route:
/**
* @Route("/profile/{id}", name="user_profile")
*/
public function viewProfile($id)
{
$user = $this->getDoctrine()->getRepository(User::class)->find($id);
return $this->render('user/profile.html.twig', ['user' => $user]);
}
Any user can modify the URL like /profile/2 and view someone else's profile. Not good.
✅ Secure version:
public function viewProfile($id)
{
$user = $this->getUser();
if ($user->getId() != $id && !$this->isGranted('ROLE_ADMIN')) {
throw $this->createAccessDeniedException();
}
$profile = $this->getDoctrine()->getRepository(User::class)->find($id);
return $this->render('user/profile.html.twig', ['user' => $profile]);
}
This enforces ownership or admin rights before allowing access.
✅ Best Practices to Prevent Broken Access Control in Symfony
-
Use
@IsGrantedordenyAccessUnlessGranted()for fine-grained permission checks. -
Avoid passing sensitive object IDs in URLs when possible.
-
Never trust client-side data like hidden fields or JavaScript-based logic.
-
Enable security.yaml configuration for routes:
access_control:
- { path: ^/admin, roles: ROLE_ADMIN }
🛡️ Scan Your Website for Broken Access Control
You can easily check your Symfony website for Broken Access Control and other critical vulnerabilities using our Website Vulnerability Scanner.
📸 Screenshot of the webpage of our Website Vulnerability Scanner tool

Screenshot of the free tools webpage where you can access security assessment tools.
Simply enter your site URL and run a scan in seconds!
📸 Screenshot of a website vulnerability assessment report generated by our free tool to check Website Vulnerability
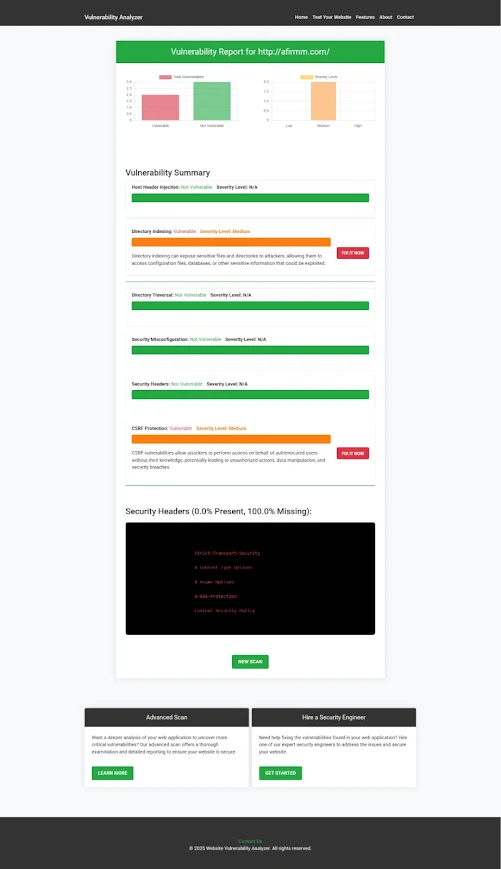 |
| An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities. |
These reports give you insight into where your app may be leaking permissions or allowing unauthorized access.
🔗 Related Security Topics on Our Blog
Explore more web security topics like:
Visit our blog at 👉 https://www.pentesttesting.com/blog/
✅ Conclusion
Broken Access Control is a top-tier threat with severe consequences. Whether it's improper role checks, insecure ID-based routing, or failure to enforce server-side validation, Symfony developers must stay proactive. Use our free tool for Website Security check and secure your application today.




Comments
Post a Comment