Prevent IDOR Vulnerabilities in Symfony Framework
Insecure Direct Object References (IDOR) is a common and critical vulnerability affecting modern web applications, including those built with Symfony. IDOR vulnerabilities occur when an application provides direct access to objects like files, database records, or URLs based on user-supplied input without proper authorization checks.
In this post, we’ll explore how IDOR vulnerabilities occur in Symfony, how attackers exploit them, and how to prevent them using practical PHP code examples. We’ll also include a link to a free website vulnerability scanner online and show how it can detect IDOR and other issues in real-time.
🔗 Check out our cybersecurity blog at Pentest Testing Corp. for more developer-focused security write-ups.
What is an IDOR Vulnerability?
IDOR happens when user input is used to reference an internal object—like a file or a database row—without proper access control. Attackers can manipulate these inputs to access data they shouldn’t.
For example, consider this URL:
https://example.com/user/profile/123
If there’s no check to ensure that the user owns profile ID 123, an attacker could change it to 124 and access another user’s data.
Symfony IDOR Vulnerability Example
Here’s a basic Symfony route that might be vulnerable to IDOR:
// src/Controller/ProfileController.php
#[Route('/user/profile/{id}', name: 'user_profile')]
public function profile($id, UserRepository $userRepository): Response
{
$user = $userRepository->find($id);
return $this->render('profile/show.html.twig', [
'user' => $user,
]);
}
Issue: There’s no check to verify that the currently logged-in user is authorized to view the profile with that ID.
How Attackers Exploit This
An attacker who is authenticated might simply change the URL:
/user/profile/1025 → /user/profile/1026
If no access control is in place, they can now view or modify data that doesn’t belong to them.
Secure Symfony Code with Authorization
To fix the vulnerability, ensure you’re comparing the ID with the currently logged-in user or using access control mechanisms.
✅ Proper Authorization Example:
#[Route('/user/profile', name: 'user_profile')]
public function profile(Security $security): Response
{
$user = $security->getUser(); // Securely fetch the logged-in user
return $this->render('profile/show.html.twig', [
'user' => $user,
]);
}
In this case, no ID is passed through the URL. The system always fetches the currently logged-in user, reducing IDOR risk.
✅ Example using Symfony Voters for Advanced Authorization:
#[Route('/admin/user/{id}', name: 'admin_view_user')]
public function viewUser(User $user, AuthorizationCheckerInterface $authChecker): Response
{
if (!$authChecker->isGranted('VIEW', $user)) {
throw new AccessDeniedException('Access Denied');
}
return $this->render('admin/user.html.twig', ['user' => $user]);
}
Then define a Voter:
// src/Security/Voter/UserVoter.php
class UserVoter extends Voter
{
protected function supports($attribute, $subject)
{
return $attribute === 'VIEW' && $subject instanceof User;
}
protected function voteOnAttribute($attribute, $subject, TokenInterface $token)
{
$currentUser = $token->getUser();
return $currentUser->getId() === $subject->getId(); // Allow only if same user
}
}
🧪 Detect IDOR with Our Free Tool
You don’t have to test manually for every possible vulnerability. Try our website vulnerability scanner to scan your Symfony applications for IDOR and other issues.
👉 Screenshot of our tool interface:
 |
| Screenshot of the free tools webpage where you can access security assessment tools. |
Figure: Scan your site with our website vulnerability scanner.
📊 Sample Vulnerability Report
Here’s a sample screenshot from our tool detecting an IDOR vulnerability in a Symfony-based app:
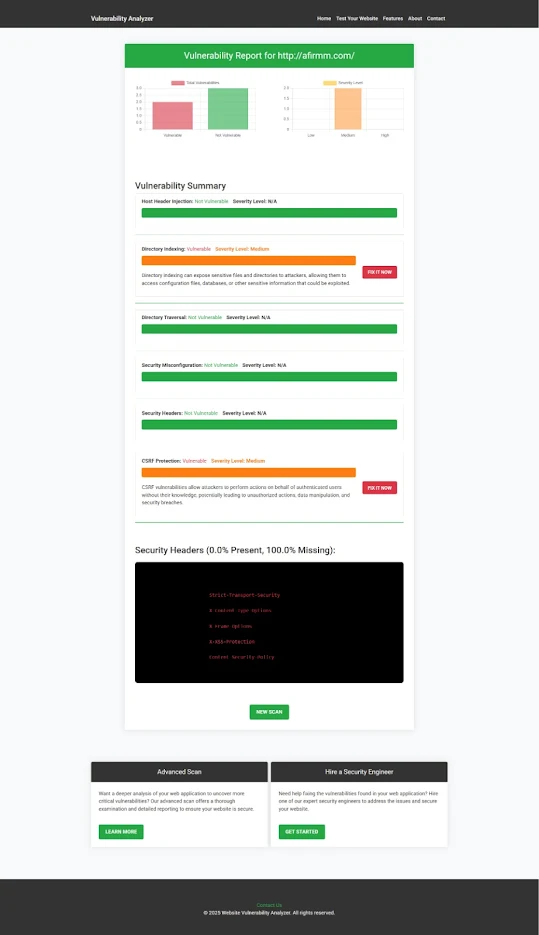 |
| An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities. |
Figure: Sample IDOR finding in the vulnerability report to check Website Vulnerability.
Key Takeaways to Prevent IDOR in Symfony
-
Never trust user input for object references.
-
Avoid exposing IDs in URLs if not needed.
-
Always verify ownership or permissions.
-
Use Symfony Security Voters or access control annotations.
-
Scan your web apps regularly for security issues.
Final Thoughts
IDOR vulnerabilities in Symfony applications are preventable with the right secure coding practices and access control. By scanning your application with tools like ours for the Website Security test, you can find and fix these vulnerabilities before attackers do.
For more posts like this, head over to Pentest Testing Corp Blog where we cover real-world security tips for developers and testers.
If you found this article helpful, feel free to share it with your developer network. And don’t forget to scan your site today—because secure code is good code.




Comments
Post a Comment