Secure Symfony: Prevent Dangerous CORS Misconfigurations
🔐 Secure CORS in Symfony: A Developer’s Guide
Implementing Cross-Origin Resource Sharing (CORS) correctly in Symfony is essential for protecting your APIs. Misconfigured CORS can expose sensitive data and open your application to Cross-Site Scripting, CSRF, and data leaks.
In this post, we'll walk through:
-
Understanding CORS and its risks
-
Common misconfigurations in Symfony
-
Secure configuration examples
-
Tools to detect CORS issues
-
Integrating our free Website Security Scanner
1. What Is CORS & Why It Matters
CORS is a browser-controlled mechanism that allows controlled cross-origin requests using headers like Access-Control-Allow-Origin and Access-Control-Allow-Methods. While powerful for microservices and SPA architectures, wildcards (*) or overly permissive headers are a common security gap.
2. Typical CORS Misconfigurations in Symfony
Using Symfony’s NelmioCorsBundle is common—but pitfalls include:
-
allow_origin: ['*']– permits any domain -
allow_headers: ['*'],allow_methods: ['*']– dangerous default -
Using
origin_regex: truewith wide permit patterns
Example of unsafe settings:
# config/packages/nelmio_cors.yaml
nelmio_cors:
defaults:
allow_origin: ['*']
allow_methods: ['GET', 'POST', 'PUT', 'DELETE', 'OPTIONS']
allow_headers: ['*']
paths:
'^/api/':
origin_regex: true
max_age: 3600
This setup effectively defeats the Same-Origin Policy and can leak sensitive user data.
3. Securing CORS in Symfony
✅ A. Configuration-Driven Fix
Use a strict settings style:
# config/packages/nelmio_cors.yaml
nelmio_cors:
defaults:
allow_origin: ['https://frontend.example.com']
allow_methods: ['GET', 'POST']
allow_headers: ['Content-Type', 'Authorization']
max_age: 3600
paths:
'^/api/':
origin_regex: false
-
No wildcards
-
Fixed trusted origins
-
Only needed HTTP methods & headers
🛡️ B. Controller-Level Fine-Grained Control
// src/Controller/ApiController.php
use Symfony\Component\HttpFoundation\Request;
use Symfony\Component\HttpFoundation\Response;
public function apiAction(Request $req): Response {
$origin = $req->headers->get('Origin');
$response = new Response(json_encode(['ok' => true]));
$allowed = ['https://frontend.example.com'];
if (in_array($origin, $allowed)) {
$response->headers->set('Access-Control-Allow-Origin', $origin);
$response->headers->set('Access-Control-Allow-Credentials', 'true');
}
return $response;
}
This approach adapts response headers based on valid origins — preventing wildcards or open patterns.
4. Detecting CORS Misconfigurations
Before deploying, check your headers manually:
curl -I https://your-api.com/api
Or automate it with our Website Vulnerability Scanner.
Below is a screenshot of our tool’s homepage showing quick access to tools:
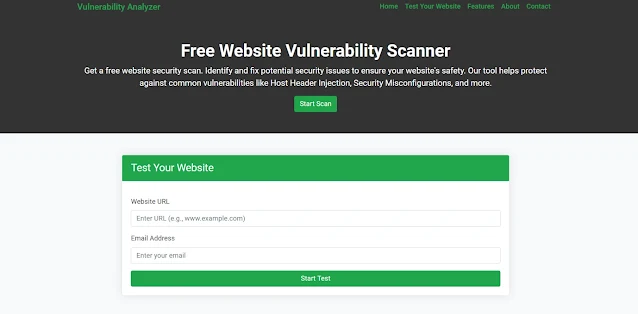 |
| Screenshot of the free tools webpage where you can access security assessment tools. |
Once scanned, you’ll receive a detailed report to check Website Vulnerability.
Here's an example of typical output:
 |
| An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities. |
Our tool flags wildcard settings and overly permissive headers, making remediation simple.
5. Why It Matters: Real-World Impact
Misconfigurations are more than theory. In 2024, a major domain registrar leaked user data across multiple API endpoints, all due to regex mismatches in CORS origin validation. Avoid the same fate with robust checks and configurations.
🛠️ Symfony Hardening Checklist
-
Avoid
*in any CORS header -
Use fixed origins or strict regex
-
Limit HTTP methods and headers
-
Test in dev, stage, and prod environments
-
Monitor using automated scans
🚀 Complementary Services from Pentest Testing Corp.
Stay informed — Subscribe on LinkedIn
✅ Take Action Today
Securing CORS isn’t optional—it's critical.
-
Audit your current Symfony CORS setup
-
Implement safe YAML or controller logic
-
Scan with our free tool at: https://free.pentesttesting.com/
-
Explore advanced cases in our official blog: https://www.pentesttesting.com/blog/
By tightening CORS policies, you're safeguarding your API and user data—now and into the future.
This post is provided by Pentest Testing Corp.




Comments
Post a Comment