Prevent SQL Injection SQLi in React.js Apps: A Practical Guide
SQL Injection (SQLi) is one of the most common and dangerous vulnerabilities in web applications. It allows attackers to manipulate SQL queries by injecting malicious SQL code, which can lead to unauthorized access to the database, data theft, and other severe consequences. In this post, we will discuss how to prevent SQL Injection in React.js applications and how you can use a free website security checker to identify vulnerabilities and fix them effectively.
In React.js, SQL Injection is generally more relevant when interacting with a backend server or database. While React itself is a front-end library and doesn’t directly interact with a database, improper handling of user inputs on the backend can expose the application to SQLi attacks. We'll walk through how to protect your React.js app from these vulnerabilities and use a website security checker to scan for potential threats.
What is SQL Injection?
SQL Injection occurs when an attacker can insert or "inject" a SQL query through user input fields. This can happen if user input is improperly sanitized before being included in SQL statements. For example, a simple login form might be vulnerable to SQL Injection if the username and password are directly inserted into an SQL query without validation.
Example of a vulnerable SQL query:
In this case, an attacker can inject malicious SQL code to bypass authentication or gain access to sensitive data.
Preventing SQL Injection in React.js
To prevent SQL Injection in React.js, follow these best practices:
1. Use Prepared Statements
Prepared statements are SQL queries that are precompiled and have placeholders for user input. This ensures that user input is treated as data, not executable code.
Example with Node.js (assuming you use a backend server with a SQL database):
By using prepared statements, SQL injection attempts are blocked, as the user input cannot alter the query structure.
2. Sanitize User Input
Make sure to sanitize all user input before using it in SQL queries. You can use libraries like express-validator or validator to clean and validate input before sending it to the server.
Example of input sanitization:
3. Limit Database Permissions
Limit the database permissions for the account used by your application. This reduces the potential damage an attacker can do if an SQLi attack is successful. For instance, avoid using an account with admin privileges for your app.
How to Test Your Application for SQL Injection Vulnerabilities
Using automated tools can help you quickly identify SQLi vulnerabilities in your React.js app. One such tool is the Pentest Testing Free Website Security Checker. It scans your website for vulnerabilities like SQL Injection, cross-site scripting (XSS), and other common security flaws.
To perform a scan, simply visit the free website security checker and enter your website URL. Once the scan is complete, you will receive a detailed vulnerability assessment report.
 |
| Screenshot of Free Website Vulnerability Scanner tool on Pentest Testing Corp. |
Example of Vulnerability Assessment Report
After scanning your React.js app with the free security checker, you will receive a comprehensive vulnerability report. It will highlight any potential SQLi flaws, misconfigurations, or security issues found on your website.
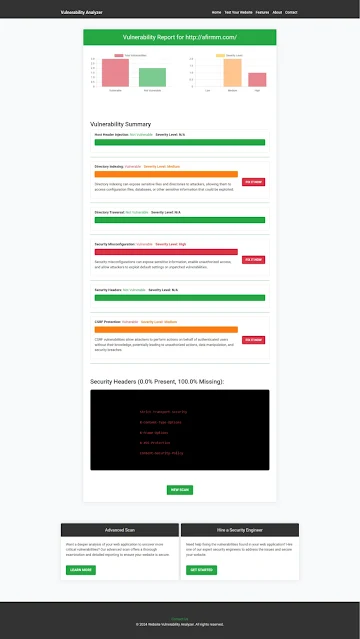 |
| Vulnerability Assessment Report Screenshot by Pentest Testing Corp.'s Free Website Vulnerability Checker tool |
Conclusion
SQL Injection is a critical vulnerability that should not be overlooked in any web application, including those built with React.js. By using best practices like prepared statements, input sanitization, and limiting database permissions, you can significantly reduce the risk of SQLi attacks. Additionally, using tools like our Free Website Vulnerability Checker helps you quickly identify and fix vulnerabilities in your React.js app.
Regularly scan your application with a website security checker, and always stay up to date with the latest security practices to ensure your web application remains secure.
Call to Action
Make sure to protect your React.js app from SQL Injection and other vulnerabilities by using the Pentest Testing Free Website Security Checker. Scan your site today and keep your data safe from attackers.
%20Vulnerabilities%20in%20React.js%20Applications.jpg)



Comments
Post a Comment