Prevent Directory Traversal Vulnerabilities in Laravel
When it comes to web application security, one of the most common threats is Directory Traversal. This vulnerability occurs when an attacker manipulates a URL or input field to access files outside the intended directory. In Laravel, a popular PHP framework, securing your application against directory traversal is essential for preventing malicious access to sensitive files.
In this blog post, we will explain directory traversal in Laravel, show you how to prevent it with code examples and demonstrate how our free Website Security Checker tool can help detect such vulnerabilities.
What is Directory Traversal?
Directory Traversal, also known as Path Traversal, is a vulnerability that allows attackers to access files and directories that are stored outside the intended directory by using a special pattern like ../../. This is especially dangerous because it can allow attackers to read sensitive files, such as configuration files or passwords.
How Directory Traversal Works in Laravel
In Laravel, the system uses routes and controllers to process user input. When user input is not properly sanitized, an attacker might be able to use directory traversal techniques to access files beyond the root directory.
Here’s an example of a vulnerable route in Laravel:
Route::get('file/{filename}', function ($filename) {
$path = storage_path('app/files/' . $filename);
return response()->file($path);
});
In this code, we are directly appending the user-provided $filename to the file path without validation. This can easily lead to directory traversal if the user provides a filename like ../../.env, which may give them access to sensitive files such as the .env configuration file.
Preventing Directory Traversal in Laravel
To prevent directory traversal in Laravel, you need to sanitize user input and use functions that restrict file access to the designated directory. Here’s an improved version of the code:
Route::get('file/{filename}', function ($filename) {
// Sanitize the filename input
$filename = basename($filename); // Removes any directory traversal patterns
$path = storage_path('app/files/' . $filename);
// Ensure the file exists and is within the correct directory
if (file_exists($path) && strpos(realpath($path), storage_path('app/files')) === 0) {
return response()->file($path);
}
abort(404); // File not found
});
In this updated code:
basename()removes any directory traversal patterns from the filename.realpath()ensures that the file is within the allowed directory.abort(404)is called if the file doesn't exist or if it's outside the allowed directory.
Testing for Directory Traversal Vulnerabilities
To make sure your Laravel application is safe from directory traversal attacks, it’s essential to regularly test your website for vulnerabilities.
You can use our tool to test website security free to scan your Laravel website and detect vulnerabilities such as directory traversal, cross-site scripting (XSS), SQL injection, and more.
Here’s a screenshot of our free website security checker tool in action:
 |
| Screenshot of the free tools webpage where you can access security assessment tools. |
By using our tool, you can get a comprehensive report of potential vulnerabilities and take action to secure your website before attackers can exploit them.
Example of a Vulnerability Assessment Report
After running the scan, you’ll receive a detailed vulnerability assessment report. This will highlight any potential issues on your website, including directory traversal vulnerabilities. Here’s an example of a report generated by our tool:
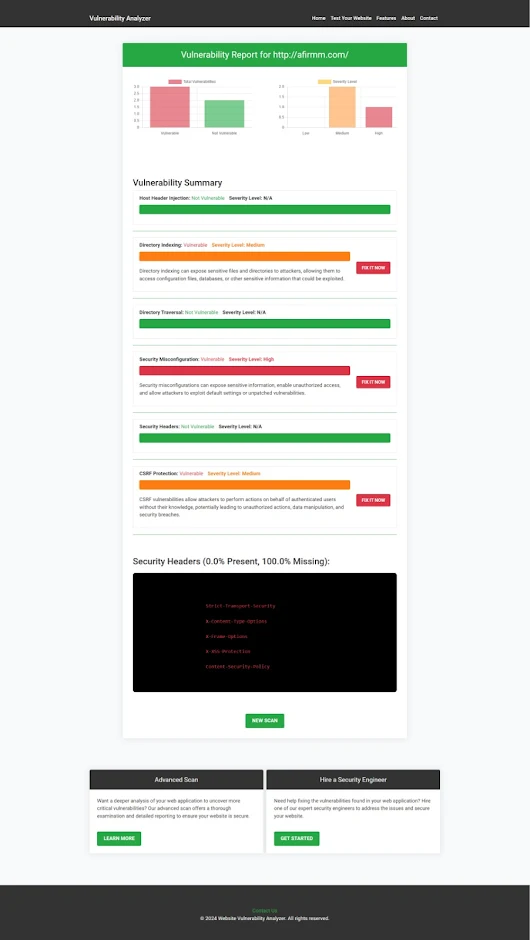 |
| Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities. |
Conclusion
Directory traversal is a serious security threat, but by following best practices in Laravel, you can prevent attackers from exploiting this vulnerability. Proper input validation, sanitization, and the use of security tools like Free Website Security Checker will help keep your Laravel application secure.
Ensure your application is thoroughly tested and secured against vulnerabilities like directory traversal to protect both your data and your users.
By implementing these security measures, you'll be able to create a more secure web application and provide a better user experience. Use our free tool to scan your website and stay ahead of potential threats!




Comments
Post a Comment