Prevent Session Fixation in Laravel: Guide & Code Example
Preventing Session Fixation in Laravel: A Comprehensive Guide
In today’s digital landscape, securing web applications is more important than ever. Session fixation is a critical vulnerability that attackers exploit to hijack user sessions. This blog post dives into what session fixation is, why it’s dangerous, and how to prevent it in your Laravel applications.
Additionally, we’ll showcase how tools like our free Website Security checker can help identify vulnerabilities and improve your website's overall security.
What Is Session Fixation?
Session fixation is an attack where the attacker sets a user's session ID to a known value. Once the user logs in, the attacker can use the same session ID to gain unauthorized access to the user’s session.
Why Is Session Fixation Dangerous?
- Unauthorized access to user accounts.
- Exposure of sensitive information.
- Potential for significant reputational damage to your application.
How Laravel Handles Session Management
Laravel provides robust tools for session management, but developers need to configure them properly to avoid vulnerabilities like session fixation.
Preventing Session Fixation in Laravel
Here are some practical steps to mitigate session fixation in Laravel:
Step 1: Regenerate Session ID After Authentication
Laravel makes it easy to regenerate the session ID once the user logs in. Add the following code to your login controller:
use Illuminate\Support\Facades\Auth;
public function login(Request $request)
{
// Validate credentials
$credentials = $request->only('email', 'password');
if (Auth::attempt($credentials)) {
// Regenerate session ID
$request->session()->regenerate();
return redirect()->intended('dashboard');
}
return back()->withErrors([
'email' => 'The provided credentials do not match our records.',
]);
}
This ensures that the session ID is refreshed upon successful login, reducing the risk of fixation.
Step 2: Use Laravel's CSRF Protection
Always use Laravel's built-in CSRF protection to prevent unauthorized actions. In your forms, include:
@csrf
Screenshot of Our Free Website Security Tool
Here’s how our Website Security Scanner can help you identify vulnerabilities, including session fixation risks.
 |
| Screenshot of the free tools webpage where you can access security assessment tools. |
Step 3: Configure Session Settings
In your Laravel application's config/session.php, ensure you’ve configured these settings:
'secure' => env('SESSION_SECURE_COOKIE', true),
'http_only' => true,
'same_site' => 'strict',
These settings enhance cookie security and prevent session hijacking.
Analyzing Vulnerabilities with Our Free Tool
After implementing these security measures, use our free Website Security checker to assess the vulnerability of your application.
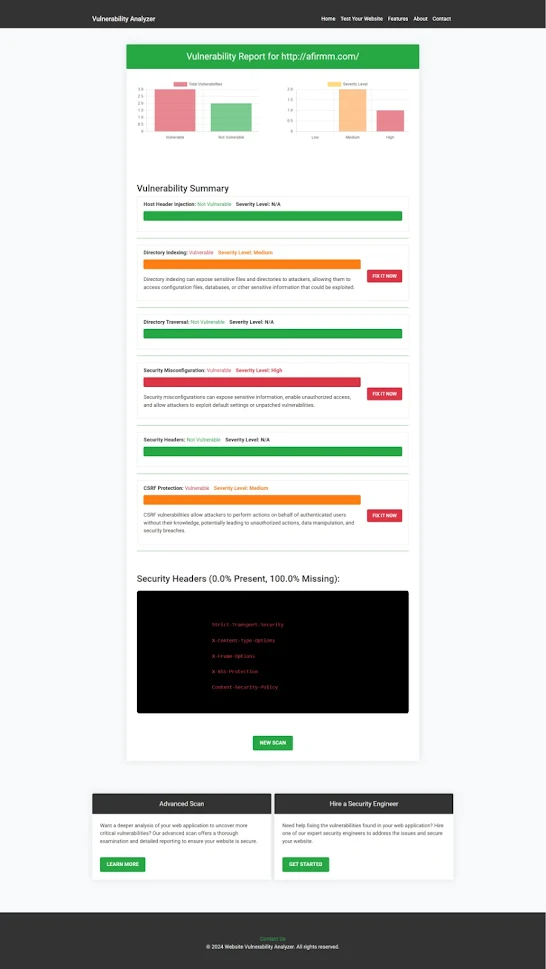 |
| An example of a vulnerability assessment report generated with our free tool provides insights into possible vulnerabilities. |
This comprehensive report provides insights into session vulnerabilities and other critical issues.
Final Thoughts
Securing your Laravel application from session fixation attacks is essential to maintaining user trust and safeguarding sensitive information. By following the steps outlined in this blog and leveraging tools like our free Website Security checker, you can take your application's security to the next level.
Start your journey to a more secure web application by visiting our tool to test your website free today.




Comments
Post a Comment