XML External Entity (XXE) Injection Vulnerability in Laravel: How to Prevent It
XML External Entity (XXE) Injection in Laravel: How to Prevent It
XML External Entity (XXE) injection is a critical vulnerability that can affect web applications that process XML input. This vulnerability allows attackers to inject malicious XML code into an application, leading to severe security risks like data theft, denial of service (DoS), and server compromise. In this blog post, we will explore how XXE injection works, demonstrate a simple code example in Laravel and discuss ways to mitigate this vulnerability.
What is XML External Entity (XXE) Injection?
XXE injection occurs when an attacker is able to manipulate an XML parser in an application by including external entities. These entities can be used to read sensitive files on the server, execute malicious code, or even perform denial-of-service attacks. For example, an attacker could craft an XML payload to read files such as /etc/passwd or perform internal network reconnaissance.
Example of XXE Injection Vulnerability:
Consider the following example of a vulnerable Laravel code snippet that processes XML input:
use Illuminate\Http\Request;
public function processXml(Request $request)
{
$xml = simplexml_load_string($request->input('xml_data'));
// Vulnerable code, as external entities are not disabled
// This can lead to XXE injection
// Further processing...
}
In this code, an XML string is being processed without disabling external entities, making the application vulnerable to XXE attacks.
How to Prevent XXE Injection in Laravel
To secure your Laravel application from XXE attacks, you need to disable the use of external entities in the XML parser. Here's how you can do it:
use Illuminate\Http\Request;
public function processXml(Request $request)
{
// Disable external entities to prevent XXE injection
libxml_disable_entity_loader(true);
// Safe XML parsing
$xml = simplexml_load_string($request->input('xml_data'), 'SimpleXMLElement', LIBXML_NOENT | LIBXML_DTDLOAD);
// Further processing...
}
In this updated version, libxml_disable_entity_loader(true) disables external entity loading, effectively protecting the application from XXE injection. Additionally, the use of LIBXML_NOENT ensures that the parser does not process external entities.
Additional Tips to Prevent XXE Vulnerabilities
- Use a Secure XML Parser: Opt for parsers that are configured to prevent XXE by default, such as
DOMDocumentwith proper configuration settings. - Validate Input Data: Always validate and sanitize input data before processing it. This minimizes the risk of malicious data being injected.
- Implement Error Handling: Proper error handling can prevent attackers from gaining insights into your application’s inner workings.
Test Your Laravel Application for Vulnerabilities
To ensure your Laravel application is secure against XXE and other vulnerabilities, use tools like Pentest Testing's Free Website Security Scanner. Our tool scans your website for common vulnerabilities, including XXE, and generates detailed reports to help you secure your web applications.
Screenshot of the Free Website Security Checker Tool:
 |
| Screenshot of the free tools webpage where you can access security assessment tools. |
By scanning your website with our free tool, you can identify any security weaknesses, including XML External Entity injection vulnerabilities, and take necessary actions to protect your application.
Screenshot of Website Vulnerability Assessment Report:
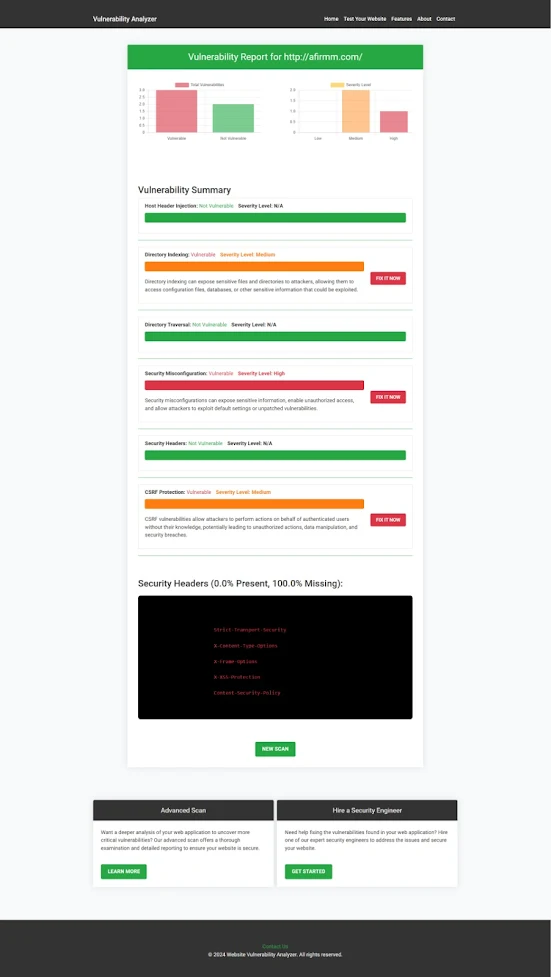 |
| Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities. |
Conclusion
XXE injection is a severe security threat that can affect Laravel applications if not properly mitigated. By disabling external entity loading and following best practices for XML parsing, you can secure your application against this vulnerability. Make sure to regularly test your website for vulnerabilities using tools like Pentest Testing's Free Website Security Checker, and stay ahead of potential threats.
Final Thoughts:
This blog post provides a thorough introduction to XXE injection, how it can be exploited in Laravel, and the steps to mitigate it. It's essential to educate your development team and continuously test for security vulnerabilities to ensure the safety of your web applications.
Make sure to optimize your code, and always use secure practices to protect user data. If you're unsure about the security of your application, try running a vulnerability scan with our tool to test website security free.
%20Injection.jpg)



Comments
Post a Comment