Prevent Business Logic Vulnerabilities in Laravel
In today's rapidly evolving digital landscape, ensuring the security of web applications is paramount. Laravel, a popular PHP framework, offers robust features for developers. However, like any framework, it's susceptible to specific vulnerabilities, notably business logic flaws.
This article delves into understanding these vulnerabilities within Laravel applications and provides actionable strategies to prevent them.
What Are Business Logic Vulnerabilities?
Business logic vulnerabilities arise from flaws in an application's design and implementation, allowing attackers to manipulate legitimate functionalities for malicious purposes.
Unlike typical security issues that exploit technical weaknesses, these vulnerabilities stem from inadequate validation, improper implementation, or flawed assumptions about user behavior.
Attackers leverage these flaws to perform unauthorized actions, leading to potential data breaches, financial losses, or reputational damage.
Common Examples in Laravel Applications
1. Excessive Trust in Client-Side Controls
Assuming users will only interact with the application through its intended interface can be dangerous. Attackers can bypass client-side validations using tools like Burp Suite, sending malicious requests directly to the server.
Example:
Consider a Laravel application where the price of a product is set on the client side:
// JavaScript code on the client side
let price = 100; // Price set on the client side
An attacker can manipulate this value before sending it to the server, leading to unauthorized price changes.
Prevention:
Always validate and set critical data, like pricing, on the server side. In Laravel, use Eloquent models to retrieve and validate product prices:
// Controller method in Laravel
use App\Models\Product;
public function purchase(Request $request, $productId)
{
$product = Product::findOrFail($productId);
$price = $product->price; // Price fetched from the server-side
// Proceed with the purchase process
}
2. Flawed Assumptions About User Behavior
Developers might assume users will follow a specific sequence of actions. Attackers can exploit these assumptions by skipping steps or accessing functionalities out of order.
Example:
In a multi-step form submission, suppose the final step doesn't re-validate data from previous steps:
// Final step controller method
public function submitFinalStep(Request $request)
{
// Assumes previous steps validated 'email' field
$email = $request->input('email');
// Process the final submission
}
An attacker can directly access this step, providing invalid or malicious data.
Prevention:
Implement comprehensive validation at each step and ensure that all necessary data is re-validated before processing.
// Final step controller method with validation
public function submitFinalStep(Request $request)
{
$validatedData = $request->validate([
'email' => 'required|email',
// Other necessary fields
]);
// Process the final submission
}
3. Domain-Specific Flaws
These vulnerabilities are unique to the application's business logic and can vary widely.
Example:
In an e-commerce platform, offering a discount code might inadvertently allow multiple uses:
// Applying discount code
public function applyDiscount(Request $request)
{
$code = $request->input('code');
$discount = Discount::where('code', $code)->first();
if ($discount) {
// Apply discount without checking usage limits
}
}
Without tracking the number of times a code has been used, an attacker can reuse it indefinitely.
Prevention:
Maintain a usage count for each discount code and enforce limits:
// Applying discount code with usage limit
public function applyDiscount(Request $request)
{
$code = $request->input('code');
$discount = Discount::where('code', $code)->first();
if ($discount && $discount->usage_count < $discount->usage_limit) {
// Apply discount
$discount->increment('usage_count');
} else {
// Inform user that the discount code is invalid or has been used up
}
}
Preventative Measures
1. Server-Side Validation
Never rely solely on client-side controls. Implement robust server-side validation using Laravel's built-in validation mechanisms to ensure all data conforms to expected formats and values.
2. Comprehensive Input Handling
Anticipate and handle unconventional inputs. For instance, ensure numeric fields are validated to accept only numbers within expected ranges:
$validatedData = $request->validate([
'quantity' => 'required|integer|min:1|max:100',
// Other fields
]);
3. Avoiding Assumptions About User Behavior
Design applications with the understanding that users may not follow the intended flow. Implement checks to enforce the correct sequence of actions.
4. Regular Security Audits
Periodically review and test your application's business logic to identify and rectify potential vulnerabilities. Utilizing automated tools can aid in this process.
For a comprehensive assessment, consider using our Website Vulnerability Scanner. This tool provides detailed reports to help you identify and address security issues effectively.
Image 1: Screenshot of the Free Website Vulnerability Scanner homepage.
 |
| Screenshot of the free tools webpage where you can access security assessment tools. |
After scanning your website to check Website Vulnerability, you’ll receive a vulnerability assessment report detailing security flaws.
Image 2: Screenshot of a website vulnerability assessment report checked by our free tool.
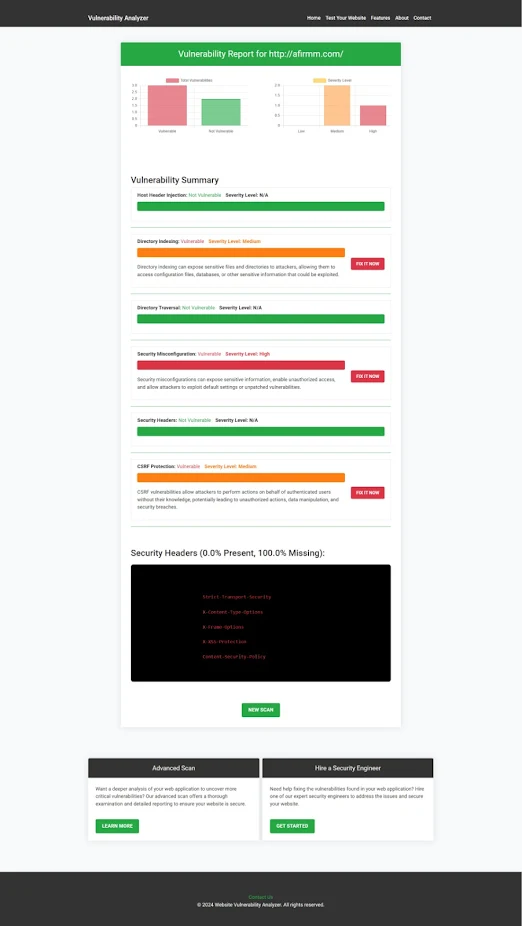 |
| An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities. |
Conclusion
Business logic vulnerabilities in Laravel applications can lead to significant security risks if left unaddressed. Developers must proactively validate inputs, enforce logical constraints, and regularly audit their applications.
By implementing these best practices and using security tools like ours for a Website Security test, you can safeguard your Laravel applications against business logic flaws.
For more cybersecurity insights and tutorials, visit our Pentest Testing Corp Blog.




Comments
Post a Comment