Prevent Command Injection in Laravel Applications: A Comprehensive Guide
Introduction
Command injection is a severe security vulnerability that can compromise the integrity of your Laravel applications. Attackers exploit this flaw by injecting malicious commands into system functions, potentially gaining unauthorized access to sensitive data, modifying system configurations, or even taking full control of a server.
Laravel applications are particularly at risk if they accept user input and pass it directly to functions like exec(), shell_exec(), or Laravel's Process::run() without proper sanitization. This article explores command injection in Laravel, how it works, and various strategies to prevent it, including secure coding practices and real-world examples.
What Is Command Injection?
Command injection occurs when an attacker manipulates user input to execute arbitrary system commands. This vulnerability is different from SQL injection, which targets databases—command injection specifically exploits an application’s ability to run shell commands.
How Attackers Exploit Command Injection
Consider the following insecure Laravel code that executes a system command using user input:
use Illuminate\Support\Facades\Process;
public function runCommand(Request $request)
{
$command = $request->input('command');
$result = Process::run("{$command}");
return $result->output();
}
Why Is This Code Vulnerable?
- The
runCommandfunction accepts input from users and directly executes it using Laravel'sProcess::run(). - If an attacker sends a specially crafted input, such as
rm -rf /, it could result in catastrophic data loss. - Malicious actors can chain multiple commands using
&&,;, or|, leading to complete system compromise.
Example of an Attack
Suppose your Laravel application provides a command-line interface where users can check server status using:
http://yourapp.com/run-command?command=ls
A malicious attacker could enter the following payload in the input field:
ls; cat /etc/passwd
If the application lacks proper input validation, it will execute both ls and cat /etc/passwd, exposing sensitive system files.
How to Prevent Command Injection in Laravel
To protect your Laravel applications from command injection, follow these security best practices.
1. Use Strict Input Validation
A robust way to mitigate command injection is by validating and restricting user inputs to a predefined set of allowed values.
Secure Example Using Laravel’s Validation Rules
use Illuminate\Support\Facades\Process;
use Illuminate\Validation\Rule;
public function runCommand(Request $request)
{
$data = $request->validate([
'command' => [
'required',
Rule::in(['uptime', 'df -h', 'whoami']), // Only allow specific safe commands
],
]);
$result = Process::run("/path/to/command {$data['command']}");
return $result->output();
}
Why Is This Safe?
- The application only permits a predefined list of commands, blocking any unauthorized ones.
- Even if an attacker tries injecting additional commands, Laravel’s validation will reject them.
2. Use escapeshellarg() and escapeshellcmd() to Escape Input
If your application must accept user input, ensure that it is safely escaped before execution.
use Illuminate\Support\Facades\Process;
public function runCommand(Request $request)
{
$command = escapeshellarg($request->input('command'));
$result = Process::run("/path/to/command {$command}");
return $result->output();
}
Why Is This Safe?
escapeshellarg()ensures that the input is treated as a single argument, preventing attackers from injecting malicious commands.
For additional safety, wrap it with escapeshellcmd():
$command = escapeshellcmd(escapeshellarg($request->input('command')));
3. Avoid Direct Execution of User Input
Whenever possible, avoid executing system commands based on user input. Instead, use Laravel’s built-in features to achieve the desired results.
Example of Alternative Approach Without System Commands
Instead of running ls via a shell command, use PHP’s built-in directory functions:
$files = scandir('/var/www/html/');
return response()->json($files);
This eliminates the need for executing system-level commands, making your application more secure.
Using Security Tools to Detect Command Injection
Proactively scanning your web application for vulnerabilities can help detect command injection risks before they become threats. Use our free tool for a quick Website Security test.
 |
| Screenshot of the free tools webpage where you can access security assessment tools. |
Our Free Website Security Scanner allows you to perform a quick and thorough security scan on your Laravel application. It can detect command injection flaws, weak input validation, and other security issues.
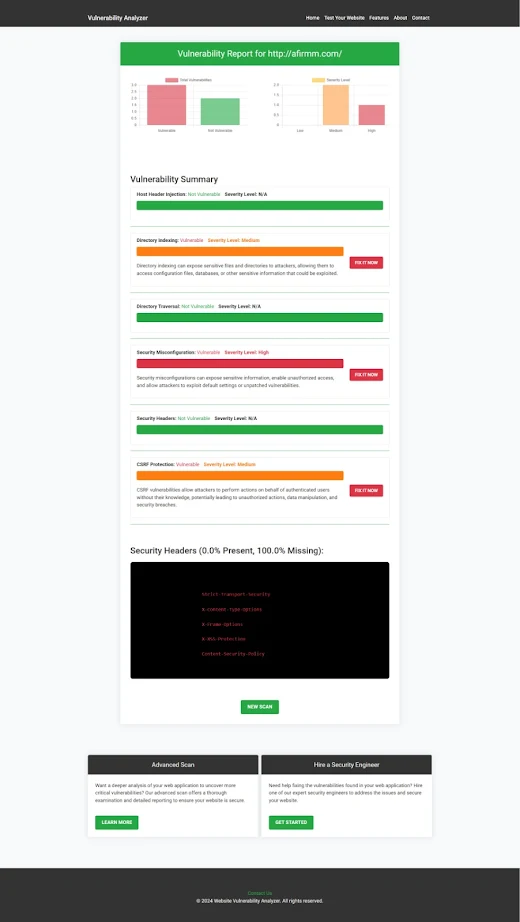 |
| An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities. |
Conclusion
Command injection is a critical security flaw that can lead to severe consequences, including unauthorized system access and data breaches. However, by implementing secure coding practices such as:
✅ Input validation using Laravel’s built-in validation rules
✅ Escaping shell arguments with escapeshellarg() and escapeshellcmd()
✅ Avoiding direct execution of user input
...you can significantly reduce the risk of command injection in your Laravel applications.
🔎 Want to test your website’s security? Use our Website Security Checker today!
For more insights and cybersecurity best practices, visit the Pentest Testing Corp blog. Stay secure! 🚀




Comments
Post a Comment