7 Proven Ways to Prevent XML Injection in Laravel
XML Injection in Laravel: A Developer’s Guide to Prevention
Introduction
XML Injection is a security vulnerability that occurs when an application improperly processes user-supplied XML input. Attackers exploit this weakness to inject malicious XML content, leading to data exposure, DoS attacks, and even remote code execution in some cases.
Laravel applications that rely on XML for data exchange (e.g., APIs, third-party integrations) must be secured against such threats. This blog explores XML Injection in Laravel, how it works, and the best ways to prevent it with secure coding practices.
📌 Before you continue: Check your website’s security with our Website Vulnerability Scanner.
What is XML Injection?
XML Injection happens when an attacker manipulates an XML input in an application to modify its structure or behavior. This can lead to:
- Unauthorized data access
- Bypassing authentication
- Denial of Service (DoS) attacks
- Server-side request forgery (SSRF)
Example of an XML Injection Attack
Consider a Laravel application that accepts XML input for processing user data:
<?xml version="1.0"?>
<User>
<Name>John</Name>
<Password>123456</Password>
</User>
If the application does not properly validate the XML input, an attacker could inject malicious XML like this:
<?xml version="1.0"?>
<User>
<Name>Attacker</Name>
<Password>malicious_code</Password>
<Token>&evil;</Token>
</User>
This could lead to unauthorized access, data modification, or application crashes.
How XML Injection Works in Laravel
Laravel applications often use PHP’s built-in SimpleXML or DOMDocument for parsing XML. If these functions process unvalidated user input, they become vulnerable to XML Injection.
Vulnerable Code Example in Laravel
if ($request->has('xml_data')) {
$xml = simplexml_load_string($request->input('xml_data'));
echo "User: " . $xml->Name;
}
🔴 Security Risk: This code does not validate or sanitize XML input, allowing attackers to inject malicious entities.
7 Proven Ways to Prevent XML Injection in Laravel
1. Disable External Entity Loading (XXE Prevention)
External XML entities can be exploited for SSRF and data exfiltration. Disable them in DOMDocument as shown below:
libxml_disable_entity_loader(true);
$xml = new DOMDocument();
$xml->loadXML($request->input('xml_data'), LIBXML_NOENT | LIBXML_DTDLOAD);
2. Use LIBXML Options for Secure Parsing
Use LIBXML_NOENT and LIBXML_DTDLOAD to prevent entity expansion attacks.
$xml = new DOMDocument();
$xml->loadXML($request->input('xml_data'), LIBXML_NOENT | LIBXML_DTDLOAD | LIBXML_NONET);
This prevents the application from fetching external resources specified in the XML.
3. Validate XML Input Before Processing
Implement XML schema validation to ensure only safe XML structures are processed:
$schema = 'path/to/schema.xsd';
if (!$xml->schemaValidate($schema)) {
die("Invalid XML format");
}
4. Escape User Input to Prevent Injection
Always escape special XML characters before processing:
$userInput = htmlspecialchars($request->input('xml_data'), ENT_QUOTES, 'UTF-8');
This prevents attackers from injecting malicious XML tags.
5. Use JSON Instead of XML (If Possible)
JSON is less prone to injection attacks compared to XML. Instead of accepting XML input, consider using JSON with Laravel’s built-in JSON validation:
$request->validate([
'json_data' => 'json',
]);
6. Restrict XML Parsing Features
Limit entity resolution to prevent XXE attacks:
$xml = new DOMDocument();
$xml->loadXML($request->input('xml_data'), LIBXML_NONET | LIBXML_NOBLANKS);
7. Monitor & Audit XML Requests
Use Laravel logging and monitoring to track suspicious XML payloads:
Log::info('XML Request: ', ['xml_data' => $request->input('xml_data')]);
🔹 Pro Tip: Regularly test your Laravel application with our free Website Security Scanner:
 |
| Screenshot of the free tools webpage where you can access security assessment tools. |
Real-World Impact of XML Injection
Imagine an e-commerce ERP system built with Laravel that uses XML for API communication. If XML Injection is not prevented, an attacker could:
✅ Extract sensitive data
✅ Manipulate transactions
✅ Execute remote code
To ensure your Laravel-based ERP is secure, follow the best practices mentioned above.
Check Your Website for Security Vulnerabilities
Do you want to know if your Laravel application is vulnerable to XML Injection or other security threats?
✅ Use our Website Security Checker to scan for vulnerabilities.
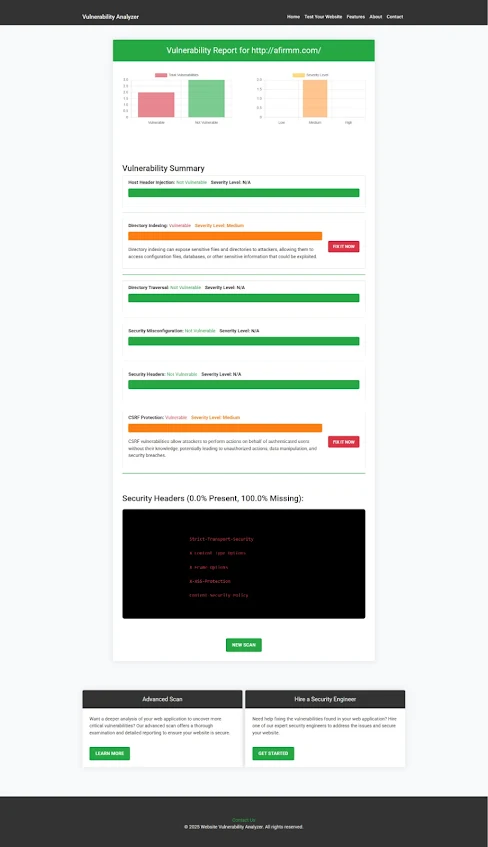 |
| An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities. |
For more insights on Laravel security, visit our blog at Pentest Testing Corp.
Conclusion
XML Injection is a serious threat that can lead to data leaks, authentication bypasses, and DoS attacks. Laravel developers must implement secure XML processing techniques, such as disabling external entities, validating input, and using JSON when possible.
💡 Take Action Now: Run a free security scan of your Laravel website and stay ahead of cyber threats!




Comments
Post a Comment