JSON Web Token (JWT) Attacks in Laravel: Prevention & Security
JSON Web Tokens (JWT) are widely used for authentication in Laravel applications. However, if not implemented securely, they can be vulnerable to various attacks. In this article, we will explore common JWT attacks in Laravel, demonstrate them with coding examples, and provide solutions to secure your application.
What is a JSON Web Token (JWT)?
A JSON Web Token (JWT) is a compact and self-contained way of transmitting information securely between two parties as a JSON object. It consists of three parts:
- Header – Contains metadata like the algorithm used (e.g., HS256, RS256).
- Payload – Contains claims (user data, permissions, etc.).
- Signature – Ensures the integrity of the token.
Example of a JWT:
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VyX2lkIjoxLCJyb2xlIjoiYWRtaW4ifQ.8zJVFZ6P74HtN2s5cR1L6XZ9CLOMWZ5q1HLmlVnpY_k
If JWT security is misconfigured in Laravel applications, attackers can exploit vulnerabilities to compromise user data.
Common JWT Attacks in Laravel
1. JWT Secret Key Brute Force Attack
If the secret key used to sign JWTs is weak, attackers can brute-force it and generate valid tokens.
Example of an Insecure JWT Configuration in Laravel (.env file):
JWT_SECRET=myweaksecret
An attacker can use tools like John the Ripper or JWT-Tool to crack weak JWT secrets.
✅ How to Fix: Use a strong, unpredictable secret key. Generate one using:
php artisan jwt:secret
Or manually set a strong key in .env:
JWT_SECRET=3R@nd0mL0nGSeCr3tKeY987!
2. JWT Token Forgery via Algorithm Manipulation
If the JWT verification process does not properly check the algorithm, an attacker can modify the token to use none as the algorithm, bypassing signature verification.
Vulnerable JWT Header Example:
{
"alg": "none",
"typ": "JWT"
}
Laravel’s tymon/jwt-auth package correctly verifies the algorithm, but if custom implementations are used, ensure algorithm enforcement:
✅ How to Fix: Always validate the JWT algorithm in Laravel:
use Firebase\JWT\JWT;
use Firebase\JWT\Key;
$jwt = "eyJhbGciOiJub25lIiwidHlwIjoiSldUIn0.eyJ1c2VyX2lkIjoxfQ.";
$decoded = JWT::decode($jwt, new Key(env('JWT_SECRET'), 'HS256'));
3. Token Expiration Bypass
If Laravel does not properly check for expired tokens, attackers can reuse old JWTs.
✅ How to Fix: Ensure tokens have a short expiration time (exp claim). Example Laravel configuration (config/jwt.php):
'ttl' => 60, // Token expires in 60 minutes
To manually check token expiration:
if ($decoded->exp < time()) {
throw new Exception("Token has expired");
}
4. JWT Injection via SQLi
If JWT payloads are used directly in SQL queries, attackers can inject malicious SQL statements.
Vulnerable Code Example:
$userId = JWT::decode($token, new Key(env('JWT_SECRET'), 'HS256'))->user_id;
$user = DB::select("SELECT * FROM users WHERE id = '$userId'");
An attacker could modify the JWT payload to execute SQL injection.
✅ How to Fix: Use parameterized queries:
$user = DB::select("SELECT * FROM users WHERE id = ?", [$userId]);
Testing Your Website Security
To ensure your Laravel application is secure against JWT attacks, perform a Website Security test using our free tool.
🔍 Example Screenshot:
 |
| Screenshot of the free tools webpage where you can access security assessment tools. |
Simply enter your website URL, and the tool will check for vulnerabilities like weak JWT secrets, insecure algorithms, and expired token misuse.
After scanning, you will receive a detailed vulnerability assessment report to check Website Vulnerability.
📊 Example Screenshot: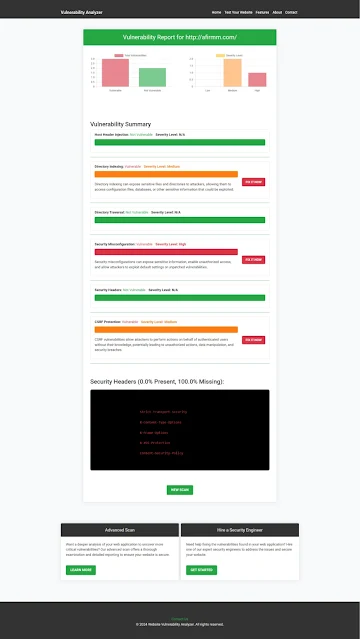
An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
Use this report to fix security issues in your Laravel application before attackers exploit them.
Final Thoughts
JWT-based authentication in Laravel is powerful but requires proper security configurations. Follow these best practices to protect your application:
✅ Use a strong secret key.
✅ Enforce a secure algorithm (HS256 or RS256).
✅ Ensure tokens expire and cannot be reused.
✅ Avoid using JWT payloads directly in SQL queries.
✅ Regularly test your application with our free Website Security Scanner.
For more cybersecurity articles, visit Pentest Testing Corp Blog.
%20Attacks%20in%20Laravel.jpg)



Comments
Post a Comment