Prevent Cross-Site Script Inclusion (XSSI) in Laravel Safely
Introduction
Cross-Site Script Inclusion (XSSI) is a security vulnerability that allows attackers to exploit the way web browsers handle script tags, potentially leading to unauthorized data access.
In this article, we'll explore what XSSI is, how it can affect Laravel applications, and provide practical coding examples to prevent such vulnerabilities.
Understanding Cross-Site Script Inclusion (XSSI)
XSSI occurs when a web application includes external scripts without proper validation, allowing attackers to inject malicious code.
This vulnerability leverages the fact that browsers do not enforce the Same-Origin Policy (SOP) on script tags, permitting cross-origin script inclusion. Consequently, sensitive data can be exposed to unauthorized parties.
Risks Associated with XSSI in Laravel
In Laravel applications, XSSI can lead to:
- Data Exposure: Sensitive information, such as user data or authentication tokens, can be accessed by unauthorized scripts.
- Unauthorized Actions: Malicious scripts can execute unintended actions within the application context.
Preventing XSSI in Laravel
To safeguard your Laravel application against XSSI attacks, consider implementing the following measures:
1. Avoid Including Untrusted Scripts
Refrain from including external scripts from untrusted sources. If inclusion is necessary, ensure the scripts are from reputable origins and served over HTTPS.
2. Implement Content Security Policy (CSP)
A robust CSP helps control which resources can be loaded by the browser, mitigating the risk of XSSI. In Laravel, you can set CSP headers in middleware:
<?php
namespace App\Http\Middleware;
use Closure;
class ContentSecurityPolicy
{
public function handle($request, Closure $next)
{
$response = $next($request);
$response->headers->set('Content-Security-Policy', "default-src 'self'; script-src 'self' https://trusted.cdn.com");
return $response;
}
}
This policy allows scripts only from your domain and a trusted CDN.
3. Sanitize User Inputs
Always sanitize and validate user inputs to prevent the injection of malicious scripts. Laravel provides built-in validation mechanisms:
$request->validate([
'username' => 'required|string|max:255',
'email' => 'required|email',
// other validations
]);
4. Use Laravel's Blade Templating Engine
Laravel's Blade engine automatically escapes output, reducing the risk of script injection:
<p>{{ $user->name }}</p>
For unescaped output, use with caution:
<p>{!! $user->bio !!}</p>
5. Leverage Security Tools
Utilize security tools to scan your application for vulnerabilities. Our Website Vulnerability Analyzer can help identify potential issues, including XSSI.
📌 Screenshot of Our Free Tools Webpage
Visual Aids
To enhance understanding, consider the following visuals:
📌 Screenshot of Our Free Tools Webpage
 |
| Screenshot of the free tools webpage where you can access security assessment tools. |
This screenshot displays our free security assessment tool you can use for Website Security check.
📌 Screenshot of a Website Vulnerability Assessment Report to check Website Vulnerability
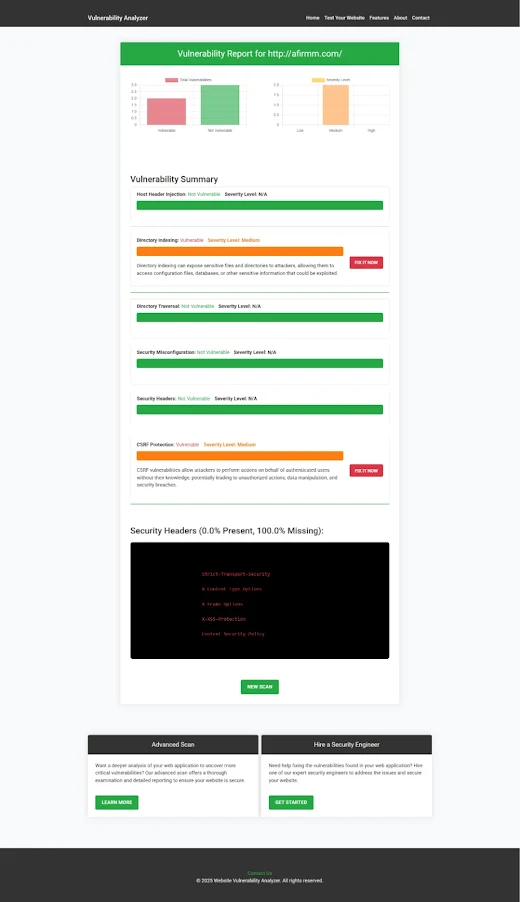 |
| An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities. |
This screenshot illustrates an XSSI vulnerability detected using our free tool.
Conclusion
Protecting your Laravel application from Cross-Site Script Inclusion (XSSI) is crucial for maintaining data integrity and user trust.
By avoiding untrusted scripts, implementing a Content Security Policy, sanitizing user inputs, utilizing Blade's templating features, and leveraging security tools, you can significantly reduce the risk of XSSI attacks.
Regular security assessments are essential to ensure ongoing protection.
For more insights into securing your applications, visit our blog at Pentest Testing Corp. 🚀
%20Vulnerabilities%20in%20Laravel%20%F0%9F%9B%A0%EF%B8%8F.jpg)



Comments
Post a Comment