Broken Authentication in Symfony: Real-World Fixes
In the world of web security, Broken Authentication remains one of the most critical and exploited vulnerabilities. If you’re working with the Symfony PHP framework, securing your authentication layer is not just good practice — it’s essential.
This blog will dive deep into how Broken Authentication can appear in Symfony applications, demonstrate vulnerable code snippets, and show you how to fix them. We’ll also walk you through how to use our free website vulnerability scanner online to detect such issues in real-time.
You can find more detailed cybersecurity articles on our official blog at Pentest Testing Corp.
🔒 What is Broken Authentication?
Broken Authentication refers to flaws in an application’s login mechanism, allowing attackers to bypass or manipulate the authentication process. This can lead to unauthorized access to sensitive data or admin functionalities.
In Symfony applications, this often occurs due to:
-
Weak or poorly implemented password checks
-
Insecure session handling
-
Not limiting login attempts
-
Not invalidating sessions after logout or password reset
🧪 Vulnerable Symfony Code Example
Let’s look at a basic login controller in Symfony that lacks rate limiting and uses a direct database lookup.
// src/Controller/LoginController.php
public function login(Request $request, EntityManagerInterface $em): Response
{
$username = $request->request->get('username');
$password = $request->request->get('password');
$user = $em->getRepository(User::class)->findOneBy(['username' => $username]);
if (!$user || !password_verify($password, $user->getPassword())) {
return new Response('Invalid credentials');
}
// Login successful
$session = $request->getSession();
$session->set('user_id', $user->getId());
return new Response('Login successful');
}
⚠️ Issues:
-
No brute-force protection
-
Insecure session handling
-
No password hashing upgrades
-
No logging or alerting on failed attempts
✅ Secure Login Implementation
Here’s how you can secure authentication in Symfony:
🔐 Use Symfony Security Component
# config/packages/security.yaml
security:
encoders:
App\Entity\User:
algorithm: auto
providers:
app_user_provider:
entity:
class: App\Entity\User
property: username
firewalls:
main:
anonymous: true
form_login:
login_path: login
check_path: login
logout:
path: logout
invalidate_session: true
access_control:
- { path: ^/admin, roles: ROLE_ADMIN }
✅ Enforcing Secure Passwords (Entity Setup)
// src/Entity/User.php
use Symfony\Component\Security\Core\User\PasswordAuthenticatedUserInterface;
class User implements PasswordAuthenticatedUserInterface
{
// ...
public function getPassword(): ?string
{
return $this->password;
}
}
🔁 Enable Session Fixation Protection
# config/packages/framework.yaml
framework:
session:
handler_id: null
cookie_secure: auto
cookie_httponly: true
use_strict_mode: true
🧰 Protecting Against Brute Force
Symfony doesn’t have native rate-limiting on login, but you can use Symfony RateLimiter Component:
use Symfony\Component\RateLimiter\RateLimiterFactory;
use Symfony\Component\HttpKernel\Exception\TooManyRequestsHttpException;
public function login(Request $request, RateLimiterFactory $loginLimiter)
{
$limiter = $loginLimiter->create($request->getClientIp());
if (false === $limiter->consume(1)->isAccepted()) {
throw new TooManyRequestsHttpException();
}
// Proceed with login logic
}
# config/packages/rate_limiter.yaml
framework:
rate_limiter:
login:
policy: 'sliding_window'
limit: 5
interval: '1 minute'
🧪 Screenshot: Free Website Security Checker
Below is a screenshot of our free website security scanner that you can use to test your Symfony-based web applications for Broken Authentication and other vulnerabilities.
 |
| Screenshot of the free tools webpage where you can access security assessment tools. |
📋 Screenshot: Website Vulnerability Report Example
Here’s an example of a detailed vulnerability assessment report to check Website Vulnerability generated by our tool after scanning a Symfony website with broken authentication flaws.
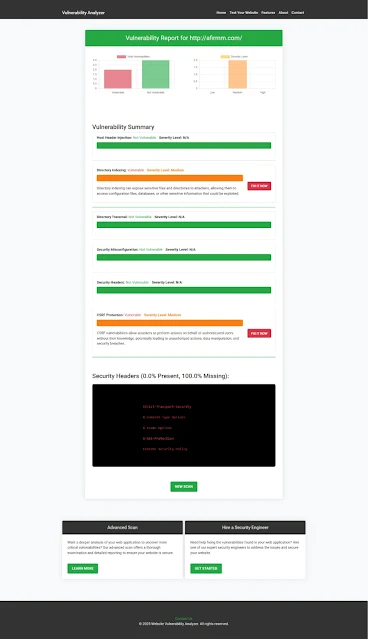 |
| An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities. |
🛡️ Final Thoughts
Broken Authentication can expose your Symfony application to serious risks, including full account takeovers. Using Symfony’s security best practices, proper session handling, rate-limiting, and regular vulnerability scanning can significantly reduce your exposure.
Before you ship any release, scan your site with our Website Vulnerability Scanner and visit our blog for more security insights at Pentest Testing Corp.




Comments
Post a Comment