Open Redirect Vulnerability in Symfony
Open Redirect Vulnerability in Symfony: Risks, Exploits & Prevention
Open Redirect vulnerabilities are often underestimated, yet they can be leveraged by attackers for phishing, social engineering, and redirect chains to malicious websites. If you're building or managing Symfony applications, understanding this vulnerability is crucial.
In this blog, we'll explore how Open Redirect works in Symfony, provide real-world code examples, and demonstrate how to test your site using our free Website Security Scanner.
🔗 Also read more about other vulnerabilities on our official blog: Pentest Testing Blog
🔍 What Is an Open Redirect Vulnerability?
An Open Redirect occurs when an application accepts a user-controlled input that specifies a link and redirects users to it without validating the destination. This allows attackers to send legitimate-looking links that redirect unsuspecting users to phishing or malicious websites.
In Symfony, this might happen when improperly handling the URL redirection logic via the redirect() helper or RedirectResponse class.
🧪 Real-World Symfony Example: Unsafe Redirection
Here’s a vulnerable Symfony controller that naively redirects based on user input:
use Symfony\Component\HttpFoundation\Request;
use Symfony\Component\HttpFoundation\RedirectResponse;
public function loginRedirect(Request $request)
{
$url = $request->query->get('next');
return new RedirectResponse($url);
}
In this case, if an attacker provides ?next=https://malicious-site.com, the application will redirect the user without verification.
🔐 Safer Code: Prevent Open Redirects in Symfony
Here’s how you can mitigate this issue using a whitelist or by verifying URLs:
✅ Method 1: Whitelist Allowed Redirects
$allowedPaths = ['/dashboard', '/settings'];
$url = $request->query->get('next');
if (in_array($url, $allowedPaths)) {
return new RedirectResponse($url);
} else {
return new RedirectResponse('/default');
}
✅ Method 2: Use Symfony Router for Validation
use Symfony\Component\Routing\RouterInterface;
public function loginRedirect(Request $request, RouterInterface $router)
{
$url = $request->query->get('next');
try {
$route = $router->match($url);
return new RedirectResponse($url);
} catch (\Exception $e) {
return new RedirectResponse('/default');
}
}
These practices help ensure that your redirection logic is robust and not easily abused.
🛡️ Test Your Site for Open Redirects
You can instantly check if your website is vulnerable using our free Website Security Checker:
📸 Screenshot: Website Vulnerability Scanner Tool
 |
| Screenshot of the free tools webpage where you can access security assessment tools. |
📸 Screenshot: Vulnerability Assessment Report Example
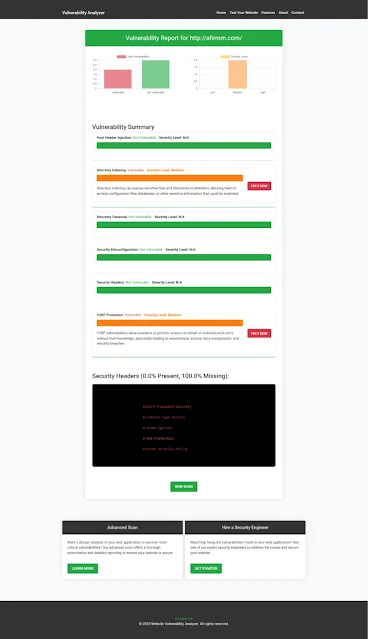 |
| An Example of a vulnerability assessment report generated with our free tool to check Website Vulnerability, providing insights into possible vulnerabilities. |
🚨 Why Open Redirects Matter
Attackers love open redirects because:
-
They bypass spam filters.
-
They lend legitimacy to phishing links.
-
They allow chaining to other vulnerabilities.
Even though the risk might seem low, the impact on brand trust and user safety is significant.
🧰 Symfony Security Tip: Use Symfony’s UrlHelper
Symfony provides utilities like UrlHelper and generateUrl() to prevent redirection to arbitrary locations. Always prefer relative URLs and use routing logic instead of trusting user input.
🧩 Additional Tips
-
Avoid using
$_GET['next']directly—always sanitize! -
For login pages, store intended routes in the session, not query strings.
-
Educate users about phishing tactics using your domain.
💼 Need Expert Help? Let Us Pentest Your Symfony App
Is your Symfony application safe from Open Redirects and other OWASP Top 10 threats?
🚀 Explore our Web App Penetration Testing Services:
👉 https://www.pentesttesting.com/web-app-penetration-testing-services/
Our team performs comprehensive vulnerability assessments, including:
-
Business Logic Testing
-
OWASP Top 10 Mapping
-
Custom Exploit Verification
-
Developer-Friendly Remediation Reports
📰 Stay Informed: Subscribe to Our Cybersecurity Newsletter
Never miss an update on critical vulnerabilities, coding tips, and security alerts!
📝 Final Thoughts:
Open Redirects are more than just a nuisance—they’re a gateway to phishing and user exploitation. Symfony developers must follow best practices for redirect handling and routinely test their applications using trusted tools.
Don’t wait for attackers to find vulnerabilities before you do—test now!



Comments
Post a Comment