How to Fix CRLF Injection Vulnerability in Laravel
Security breaches in web applications are constantly evolving, and one such threat is CRLF Injection. It occurs when an attacker injects special characters (Carriage Return and Line Feed) into HTTP headers, leading to severe vulnerabilities like HTTP response splitting and web cache poisoning. In this guide, we'll explain how CRLF injection affects Laravel apps and provide practical code examples for preventing such attacks.
You can also scan your Laravel application using our tool for a Website Security test—it’s free!
📌 What is CRLF Injection?
CRLF Injection is a vulnerability where an attacker inserts \r (Carriage Return) and \n (Line Feed) characters into the HTTP headers. These characters are used by the HTTP protocol to signify the end of headers, allowing attackers to add malicious data or split the response in a way that affects the server’s behavior.
How Does CRLF Injection Affect Laravel?
In Laravel, improper handling of user inputs, especially when redirecting or manipulating headers, can lead to CRLF injection. Without proper validation and sanitization, attackers could exploit this to send malicious cookies or headers, resulting in various attacks such as session fixation, cross-site scripting (XSS), and more.
💥 Example of a Vulnerable Laravel Route
Here's a simple example of a vulnerable route that can be exploited via CRLF injection:
Route::get('/redirect', function (Request $request) {
$url = $request->input('url');
return redirect($url);
});
An attacker can use the following URL to inject CRLF characters and manipulate the HTTP headers:
/redirect?url=http://example.com%0D%0ASet-Cookie:%20malicious=true
In this case, Laravel redirects the user but also adds a malicious Set-Cookie header due to the CRLF characters.
🛡️ How to Prevent CRLF Injection in Laravel
✅ Validate and Sanitize User Inputs
Always sanitize input parameters, particularly URLs, before using them in headers. Here’s an updated version of the route that validates the URL:
Route::get('/redirect', function (Request $request) {
$url = $request->input('url');
if (!filter_var($url, FILTER_VALIDATE_URL)) {
abort(400, 'Invalid URL');
}
return redirect($url);
});
✅ Whitelist Allowed Redirect Domains
Another best practice is to whitelist trusted domains for redirections. This limits the attack surface for CRLF injection:
$allowedHosts = ['example.com', 'myapp.com'];
$parsedUrl = parse_url($url);
if (!in_array($parsedUrl['host'] ?? '', $allowedHosts)) {
abort(403, 'Unauthorized redirect');
}
By enforcing domain validation, you can prevent attackers from redirecting users to malicious websites.
🔒 Using Laravel Middleware to Protect Headers
A more advanced approach is to create middleware that inspects headers before they are sent. The middleware checks for unsafe characters like \r or \n, aborting the request if any suspicious data is detected:
public function handle($request, Closure $next)
{
$response = $next($request);
foreach ($response->headers->all() as $name => $values) {
foreach ($values as $value) {
if (preg_match("/[\r\n]/", $value)) {
abort(400, 'Invalid header injection attempt.');
}
}
}
return $response;
}
This middleware can be applied globally or selectively to routes where header manipulation is sensitive.
🧪 Scan Your Site for Vulnerabilities Using Our Free Tool
To ensure your Laravel app is safe from CRLF Injection and other security vulnerabilities, use our Website Vulnerability Scanner Tool.
This tool automatically scans your site for common security flaws, including CRLF injection, and provides actionable insights to fix them.
 |
| Screenshot of the free tools webpage where you can access security assessment tools. |
You can use this screenshot to showcase the simplicity of the tool's interface, making it easy for anyone to scan their website for vulnerabilities.
📋 Real-World Example of a Vulnerability Assessment
Below is an example of a vulnerability assessment report generated by our free website security scanner. It highlights the CRLF injection found in a sample Laravel app:
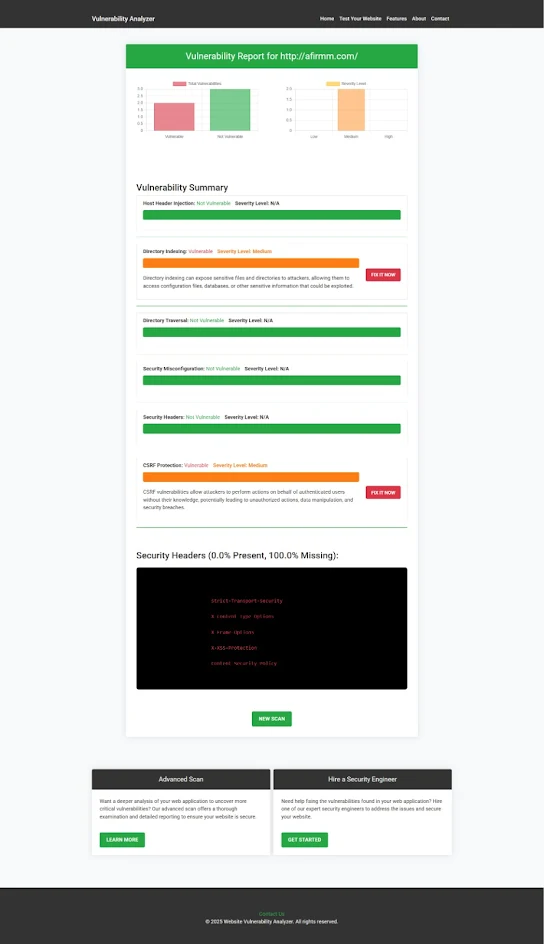 |
| An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities. |
In this example, the report shows that CRLF injection was detected, including the exact location and a detailed description of the issue.
🔗 Learn More and Stay Updated
Want more practical guides on web security and Laravel? Check out our blog at Pentest Testing Corp, where we post frequent updates on how to secure your web applications and tackle emerging threats.
🧠 Conclusion
CRLF Injection is a subtle yet potentially harmful vulnerability in Laravel apps. By properly validating and sanitizing user inputs, and utilizing middleware for additional protection, you can significantly reduce the risk of such attacks. Don’t wait for an attack—scan your site today using Pentest Testing’s free security tool and keep your Laravel app secure.




Comments
Post a Comment