Prevent CSRF Attacks in Symfony with Real Examples
Cross-Site Request Forgery (CSRF) is one of the most overlooked yet dangerous web security vulnerabilities. It allows an attacker to trick users into executing unwanted actions on a web application in which they're authenticated. If you're using the Symfony framework, it's crucial to implement robust CSRF protection to keep your application secure.
In this post, we’ll explore how CSRF vulnerabilities manifest in Symfony, how to exploit them, and most importantly—how to prevent them. We'll also include code samples and demonstrate how you can assess your website for free using our Website Vulnerability Scanner.
🔍 What is CSRF?
CSRF tricks a user’s browser into sending a forged request to a website that trusts the user. For example, if you're logged into a bank account, an attacker could craft a malicious link that performs actions on your behalf without your consent.
⚠️ CSRF in Symfony: How It Happens
Symfony provides CSRF protection via the CsrfTokenManagerInterface. However, it must be properly integrated in your forms and endpoints. Here's how a vulnerable form might look:
// Vulnerable Symfony Form without CSRF Token
<form action="/update-profile" method="POST">
<input type="text" name="email" value="user@example.com">
<input type="submit" value="Update">
</form>
If this form doesn’t implement a CSRF token, attackers can forge requests that perform profile updates or worse.
✅ How to Prevent CSRF in Symfony
Symfony offers built-in CSRF protection. You just need to enable and include the CSRF token in your forms.
🛡️ Example 1: Enabling CSRF Protection in Forms
use Symfony\Component\Form\Extension\Core\Type\FormType;
use Symfony\Component\Form\Extension\Core\Type\TextType;
use Symfony\Component\Form\Extension\Core\Type\SubmitType;
$builder = $this->createFormBuilder()
->add('email', TextType::class)
->add('save', SubmitType::class)
->getForm();
Make sure your form is generated using Symfony’s Form component. Then, enable CSRF protection in your config/packages/framework.yaml file:
framework:
csrf_protection: true
Symfony will now automatically generate and verify CSRF tokens.
🧪 Example 2: Manually Verifying a CSRF Token
If you're not using Symfony Forms, you can manually validate the CSRF token:
use Symfony\Component\Security\Csrf\CsrfToken;
use Symfony\Component\Security\Csrf\CsrfTokenManagerInterface;
public function updateAction(Request $request, CsrfTokenManagerInterface $csrfTokenManager)
{
$submittedToken = $request->request->get('_csrf_token');
if (!$csrfTokenManager->isTokenValid(new CsrfToken('update_profile', $submittedToken))) {
throw new AccessDeniedException('Invalid CSRF token.');
}
// Proceed with the update logic
}
Generate the token in your template:
<input type="hidden" name="_csrf_token"
value="{{ csrf_token('update_profile') }}">
🛠️ CSRF Testing & Prevention Made Easy
You can easily check if your Symfony application is vulnerable to CSRF and other issues using our free Website Security Scanner. It detects CSRF risks, missing tokens, and unsafe form configurations.
📸
 |
| Screenshot of the free tools webpage where you can access security assessment tools. |
The tool analyzes common web vulnerabilities including CSRF, XSS, SQL Injection, and more. After scanning, you'll receive a detailed vulnerability report to check Website Security.
📸
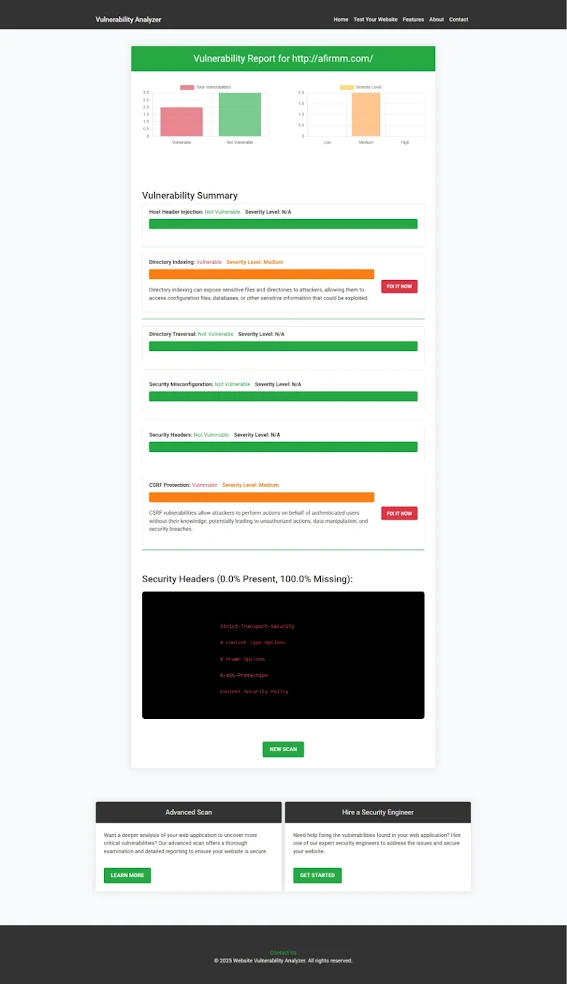 |
| An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities. |
These reports help developers fix critical security flaws quickly and effectively.
📌 Final Thoughts
CSRF is a serious threat that often flies under the radar. Fortunately, Symfony gives developers the tools to prevent it—but it's up to you to implement them correctly. Whether through the form builder or manual verification, ensuring every state-changing request is protected by a CSRF token is essential.
Regularly scan your site using free tools for a Website Security test and stay ahead of attackers.
🔗 Also Read:
Explore more cybersecurity blog posts and tutorials at Pentest Testing Corp.
If you found this post helpful, feel free to share it on social media, and don’t forget to scan your website today—it’s completely free and takes less than 60 seconds!




Comments
Post a Comment