Prevent DNS Rebinding in Symfony: Secure Your App
🔐 What Is a DNS Rebinding Attack?
DNS rebinding exploits browser DNS resolution, letting attackers point a trusted domain to internal IPs—bypassing same-origin policies to penetrate private networks.
Common real-world threats include targeting IoT devices, admin dashboards, or local APIs that don't validate the Host header.
✅ Why Symfony Apps Should Care
Symfony apps often serve APIs or admin pages trusted by *.myapp.com. An attacker could rebind evil.com to 192.168.0.10 (your internal API) and trick a browser into making authenticated requests. Without proper checks, your app treats these as legitimate. 😱
🛡️ Defense #1: Hostname Whitelisting via Middleware
Use a Symfony HTTP middleware to validate incoming Host headers:
// src/EventListener/HostValidationListener.php
namespace App\EventListener;
use Symfony\Component\HttpKernel\Event\RequestEvent;
use Symfony\Component\HttpFoundation\Response;
class HostValidationListener
{
private array $allowedHosts;
public function __construct(array $allowedHosts = [])
{
$this->allowedHosts = $allowedHosts;
}
public function onKernelRequest(RequestEvent $event): void
{
$host = $event->getRequest()->getHost();
if (!in_array($host, $this->allowedHosts, true)) {
$event->setResponse(new Response('Forbidden host', Response::HTTP_FORBIDDEN));
}
}
}
Register this listener:
# config/services.yaml
services:
App\EventListener\HostValidationListener:
tags:
- { name: kernel.event_listener, event: kernel.request, priority: 255 }
arguments:
$allowedHosts: ['myapp.com', 'api.myapp.com']
🧪 Defense #2: Symfony Firewall & Trusted Proxies
Symfony’s trusted_hosts feature adds another layer:
# config/packages/framework.yaml
framework:
trusted_hosts: ['^myapp\.com$', '^api\.myapp\.com$']
This setting rejects requests with non-matching hosts early in the process.
🌐 Defense #3: HTTPS + Proper DNS & DNS Resolver
-
Enable HTTPS: The browser checks the SSL certificate for host authenticity.
-
DNS layer: Use DNS resolvers that reject private or non-routable IPs for public domains.
-
Configure DNS TTL and CNAME chains cautiously to avoid rebinding vulnerabilities.
🛠️ Testing & Monitoring
Try our Website Vulnerability Scanner to uncover host mismatch or DNS-based vulnerabilities.
 |
| Screenshot of the free tools webpage where you can access security assessment tools. |
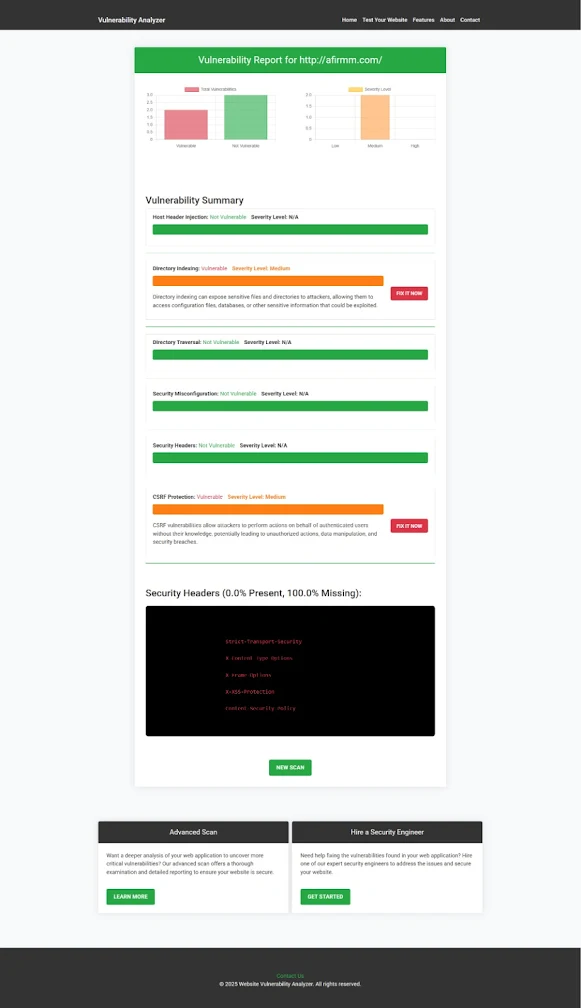 |
| An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities. |
-
The free tools interface
-
A detailed assessment report to check Website Vulnerability
💡 Bonus Tips
-
Avoid wildcard DNS entries like
*.app.local. -
Encourage DNS pinning and internal DNS rebind protection.
-
Use network segmentation and internal K8s
ClusterIPso hosts aren't publicly reachable.
🔗 Related Resources from Pentest Testing Corp
-
Explore our web app penetration testing: Web App Pentest Services
-
Offer security services to your client: Cybersecurity Service Offering
-
Read more on our blog: Pentest Testing Corp Blog
-
Stay updated! Subscribe on LinkedIn
🧠 Final Thoughts
Blocking unauthorized hosts, validating headers, and using HTTPS with proper DNS are powerful mitigations against DNS rebinding in Symfony. Combined with the free Pentest Testing tool, these defenses significantly strengthen your app against hidden network-based threats.
Secure your Symfony app now—and stay one step ahead.




Comments
Post a Comment