Secure Symfony: Fix Weak SSL/TLS Configurations in Symfony Apps
🚨 Why Hardening SSL/TLS Matters in Symfony
Weak SSL/TLS configurations expose your Symfony application to vulnerabilities like:
-
Downgrade attacks (e.g., POODLE, BEAST)
-
Man-in-the-middle interceptions
-
Breakage of Perfect Forward Secrecy (PFS)
Symfony relies on your web server or a reverse proxy for SSL. That’s why properly configuring TLS at that layer is vital. Tools like Qualys SSL Labs or our free Pentest Testing Website Vulnerability Scanner can uncover:
-
Supported protocol versions (e.g., TLS 1.0, 1.1)
-
Weak cipher suite support
-
Misconfigured settings like compression, session tickets
🔧 Step 1: Choose Strong Protocols & Ciphers
Use only TLS 1.2+, disable older versions and weak ciphers. Mozilla provides reliable cipher-suite configurations, for example:
SSLProtocol all -SSLv3 -TLSv1 -TLSv1.1
SSLCipherSuite ECDHE-ECDSA-AES256-GCM-SHA384:...
SSLHonorCipherOrder on
SSLCompression off
SSLSessionTickets off
Or in Nginx:
ssl_protocols TLSv1.2 TLSv1.3;
ssl_ciphers HIGH:!aNULL:!MD5;
ssl_prefer_server_ciphers on;
ssl_session_tickets off;
These settings disable outdated protocols and enforce modern ciphers and PFS.
🔧 Step 2: Apply to Symfony’s Built‑in Server (Dev)
Even in development, it's beneficial to use HTTPS with secure configs:
symfony server:ca:install
symfony server:start --daemon
Symfony's local server will then support TLS with trusted certs and let you focus on actual business logic.
🔧 Step 3: Enforce HTTPS in Symfony Code
Add middleware or event listener to force HTTPS and leverage HSTS:
// src/EventListener/HttpsRedirectListener.php
namespace App\EventListener;
use Symfony\Component\HttpKernel\Event\RequestEvent;
class HttpsRedirectListener
{
public function onKernelRequest(RequestEvent $event)
{
$request = $event->getRequest();
if (!$request->isSecure()) {
$event->setResponse(
new RedirectResponse(
'https://' . $request->getHttpHost() . $request->getRequestUri()
)
);
}
}
}
Add to services.yaml:
services:
App\EventListener\HttpsRedirectListener:
tags:
- { name: kernel.event_listener, event: kernel.request, priority: 100 }
Also, set HSTS headers:
$response->headers->set('Strict-Transport-Security', 'max-age=31536000; includeSubDomains; preload');
✅ Step 4: Test with Free Pentest Tool
Run a scan using our free tool to check Website Vulnerability:
 |
| Image: Pentest Testing's free Website Security Checker homepage |
Then get a vulnerability report featuring weak TLS flags:
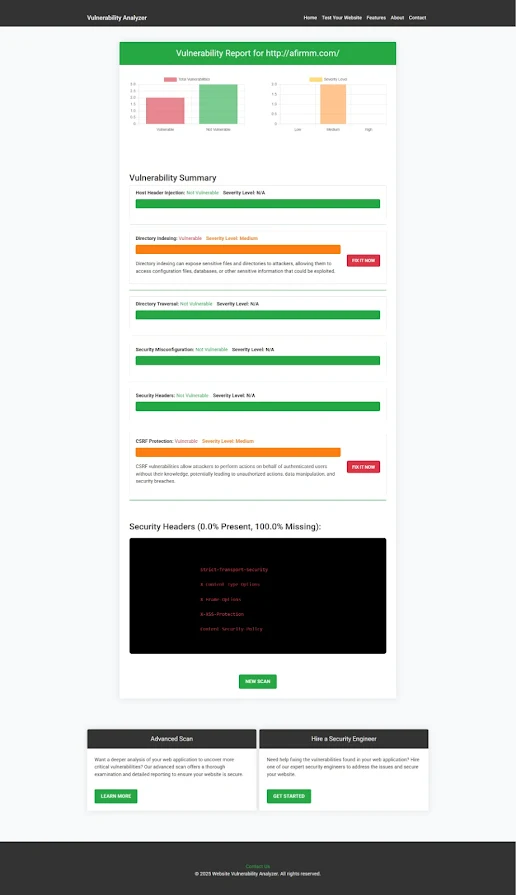 |
Image: Sample vulnerability assessment report from our free Website Security Scanner tool |
🛠️ Sample Symfony + Symfony Local Server Setup
composer create-project symfony/skeleton secure-app
cd secure-app
symfony server:ca:install
symfony server:start
Access via https, verify TLS configuration in browser dev tools, and scan with SSL Labs or our free tool.
🧩 Additional Symfony Security Best Practices
-
Use CSP, X-Content-Type-Options, and secure cookie flags
-
Store secret keys safely, avoid verbose error display
-
Disable weak TLS if deploying on platforms like Ibexa Cloud
Full hardened checklist available from the Symfony Cheat Sheet and OWASP .
🔗 Explore More Resources
-
New Web App Penetration Testing Services:
Visit our landing page -
Stay updated—Subscribe to our LinkedIn newsletter:
Subscribe on LinkedIn
✅ Summary
By configuring only secure protocols and ciphers, enforcing HTTPS, using HSTS, and regularly scanning, you’ll eliminate weak TLS in Symfony. Perfect forward secrecy, HSTS, and robust cipher suites are key steps toward a secure ramp-up. And with our free tool and premium services, Pentest Testing has you covered!
Happy securing! 🔒




Comments
Post a Comment