Command Injection in Symfony: How to Detect & Prevent It
Command injection is one of the most dangerous web application vulnerabilities today. If left unchecked, it allows attackers to execute arbitrary system commands on your server — putting your application, data, and users at risk.
In this post, we’ll explore how command injection works in Symfony applications, provide real code examples, and show you how to identify these vulnerabilities using our Website Vulnerability Scanner online free.
You’ll also learn how to harden your Symfony application against this threat, while accessing professional-grade tools and services to protect your infrastructure.
🚨 What is Command Injection?
Command injection occurs when user input is improperly handled in a way that allows execution of system-level commands. In Symfony, this often happens when unsafe data is passed directly to functions like:
-
shell_exec() -
exec() -
system() -
passthru() -
or even through third-party processes invoked from controllers.
An attacker can exploit this by injecting malicious shell commands into form fields, query parameters, or headers.
🧪 Real-Life Example: Vulnerable Symfony Code
Here’s an example of insecure Symfony controller code that is vulnerable to command injection:
// src/Controller/SecurityScanController.php
use Symfony\Bundle\FrameworkBundle\Controller\AbstractController;
use Symfony\Component\HttpFoundation\Request;
use Symfony\Component\HttpFoundation\Response;
class SecurityScanController extends AbstractController
{
public function scan(Request $request): Response
{
$domain = $request->query->get('domain');
// 🚨 DANGEROUS: Unsafe command execution
$output = shell_exec("ping -c 1 " . $domain);
return new Response("<pre>$output</pre>");
}
}
If an attacker accesses your endpoint with a payload like:
https://yourapp.com/scan?domain=google.com;ls
They can execute unintended commands like ls (list directory), and even worse — rm -rf /.
🛡️ Secure Alternative (with Symfony Process Component)
Let’s rewrite the code using Symfony’s Process component — a much safer approach.
use Symfony\Component\Process\Process;
use Symfony\Component\Process\Exception\ProcessFailedException;
public function scan(Request $request): Response
{
$domain = escapeshellarg($request->query->get('domain'));
$process = new Process(['ping', '-c', '1', $domain]);
try {
$process->mustRun();
$output = $process->getOutput();
} catch (ProcessFailedException $exception) {
$output = 'Error: Command failed.';
}
return new Response("<pre>$output</pre>");
}
Here’s what we changed:
✅ Escaped user input using escapeshellarg()
✅ Used Symfony’s Process to separate command and arguments
✅ Handled process failures gracefully
🔍 Scan Your Website for Free
Want to know if your Symfony or PHP-based site is vulnerable to command injection?
Use our free Website Security Checker tool now:
🖼️ Our Website Vulnerability Scanner Homepage:
 |
| Screenshot of the free tools webpage where you can access security assessment tools. |
🖼️ Sample Assessment Report from our tool to check Website Vulnerability:
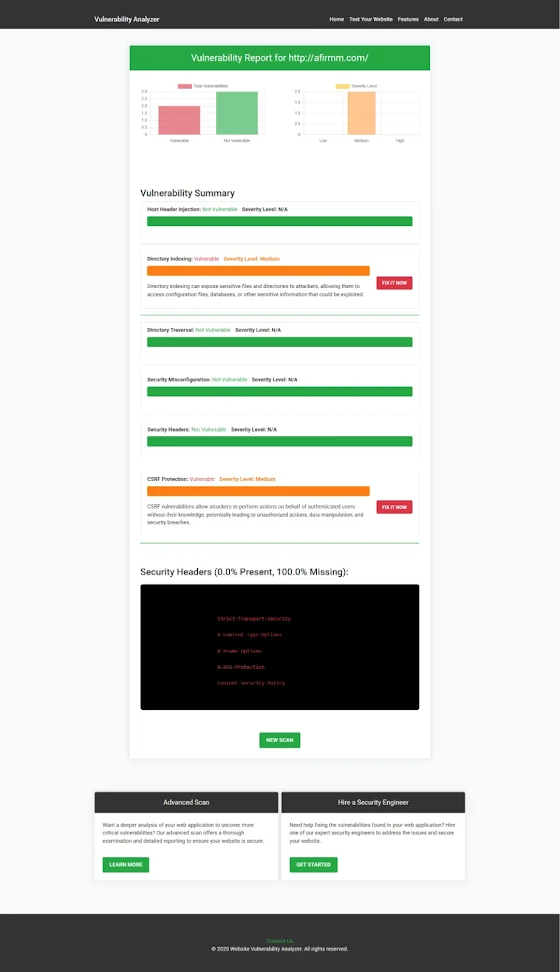 |
| An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities. |
Visit: https://free.pentesttesting.com
This tool checks for critical vulnerabilities, including command injection, XSS, insecure headers, and more — in just seconds!
🔧 Best Practices to Prevent Command Injection
-
✅ Always sanitize and validate user inputs
-
🚫 Never concatenate user input into shell/system commands
-
🧰 Use Symfony’s Process component or prepared functions
-
🔐 Implement strict Content Security Policy (CSP) headers
-
🧪 Regularly perform vulnerability assessments
🔗 Useful Symfony Functions & Filters
Below are Symfony tools and practices that help mitigate injection risks:
| Symfony Tool | Purpose |
|---|---|
| Process Component | Safe shell execution |
| Validator Component | Input validation |
| Escaper Component | Escapes dangerous input |
| Security Bundle | User access & roles |
You can also apply a custom Input Sanitizer service that filters user input across forms and API endpoints.
🧰 Advanced Protection: Let the Experts Handle It
We offer deep-dive Web App Penetration Testing Services for your Symfony, Laravel, and Node.js applications.
📌 Learn more:
🔗 https://www.pentesttesting.com/web-app-penetration-testing-services/
🤝 Offer Cybersecurity Services to Your Clients?
If you’re an agency or developer offering services to clients, you can now white-label our security expertise.
📌 Check it out:
🔗 https://www.pentesttesting.com/offer-cybersecurity-service-to-your-client/
This is a great way to boost your service offerings while ensuring your clients stay protected.
📰 Stay Updated: Free Cybersecurity Newsletter
Subscribe to our newsletter on LinkedIn for weekly insights, vulnerability alerts, and best practices.
🔗 Subscribe here: https://www.linkedin.com/build-relation/newsletter-follow?entityUrn=7327563980778995713
🔎 More from Our Blog
Want more insights like this?
📰 Browse more articles at: https://www.pentesttesting.com/blog/
We regularly publish technical breakdowns on web security, penetration testing tips, coding best practices, and vulnerability writeups.
✅ Final Thoughts
Command injection vulnerabilities are often subtle but highly dangerous. Symfony gives you powerful tools to write secure code — but it’s your responsibility to use them correctly.
Run a scan today for the Website Security test using our free tool and see if your application passes the test.
💬 Have questions or need help securing your Symfony app?
📩 Want a free scan? DM me or check https://free.pentesttesting.com/




Comments
Post a Comment