Prevent Buffer Overflow in Symfony: Best Practices & Code Examples
Buffer overflows remain one of the oldest yet most dangerous vulnerabilities in web applications. If left unchecked, attackers can exploit these flaws to crash your application, execute arbitrary code, or even gain unauthorized access. In this blog, we’ll dive deep into how you can prevent buffer overflow in Symfony, backed with coding examples, and show you how to verify your defenses using our website vulnerability scanner online free.
✅ Also check out our other security insights on the Pentest Testing Blog.
🚨 Why Buffer Overflow Matters in Web Applications
Buffer overflow occurs when a program writes more data to a buffer than it can hold. Even though PHP and Symfony are higher-level frameworks, unsafe handling of user inputs, binary data processing, or legacy C-extensions can expose you to buffer overflows.
Attackers can:
-
Crash your app (DoS).
-
Overwrite memory and execute arbitrary code.
-
Escalate privileges.
That’s why secure coding and input validation are critical.
🔒 Best Practices to Prevent Buffer Overflow in Symfony
Let’s walk through practical measures and code examples to secure your Symfony application.
1️⃣ Use Symfony Validators for Input Length
One of the easiest ways to avoid buffer overflow is by limiting the length of user inputs explicitly.
// src/Entity/User.php
use Symfony\Component\Validator\Constraints as Assert;
class User
{
/**
* @Assert\Length(
* max = 255,
* maxMessage = "Username cannot be longer than {{ limit }} characters"
* )
*/
private $username;
}
✅ This ensures no data overflows your database columns or memory buffer.
2️⃣ Use Parameter Binding and Size Constraints in Doctrine
Never let raw SQL handle unchecked data. Instead, bind parameters and enforce lengths.
$conn = $entityManager->getConnection();
$sql = 'INSERT INTO logs (message) VALUES (:message)';
$stmt = $conn->prepare($sql);
$message = substr($inputMessage, 0, 500); // trim to 500 chars
$stmt->bindValue('message', $message);
$stmt->executeStatement();
3️⃣ Filter Binary and File Uploads Safely
Buffer overflows can also happen when handling binary data.
use Symfony\Component\HttpFoundation\File\UploadedFile;
public function upload(UploadedFile $file)
{
if ($file->getSize() > 1048576) { // limit to 1MB
throw new \Exception("File too large");
}
$file->move('/uploads', $file->getClientOriginalName());
}
🖼️ Check Your Website Vulnerabilities for Free
After applying these changes, you can verify your Symfony app with our Website Vulnerability Scanner.
👉 Here’s how the tool looks:
 |
| Screenshot of the free tools webpage where you can access security assessment tools. |
When you scan your site for a Website Security test, you’ll get a report like this:
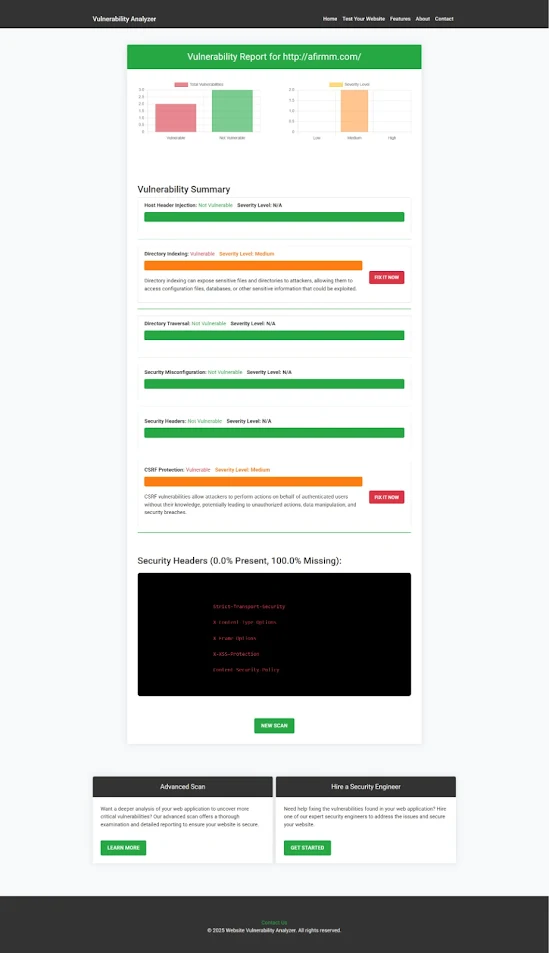 |
| An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities. |
Run your site scan here: https://free.pentesttesting.com/
🌐 Our Web Application Penetration Testing Services
Need a deeper security assessment beyond buffer overflow protection? Hire our experts to perform comprehensive web application penetration testing tailored to your stack.
🔗 Learn more: Web App Penetration Testing Services
🤝 Partner With Us to Offer Cybersecurity to Your Clients
If you’re an agency or consultant, we can help you offer cybersecurity services to your clients under your brand.
🔗 Explore: Offer Cybersecurity Service to Your Client
📬 Stay Updated With the Latest Security Tips
Don’t miss out on the latest security trends, tips, and vulnerabilities.
🔗 More Reading
Check out more technical guides on our blog: Pentest Testing Blog
Summary:
By following these Symfony coding best practices and proactively scanning your website using our tool to check Website Vulnerability, you can significantly lower the risk of buffer overflow and other security vulnerabilities in your web application.




Comments
Post a Comment